Cyber risk monitoring for your company
Continuous cyber risk monitoring for your company
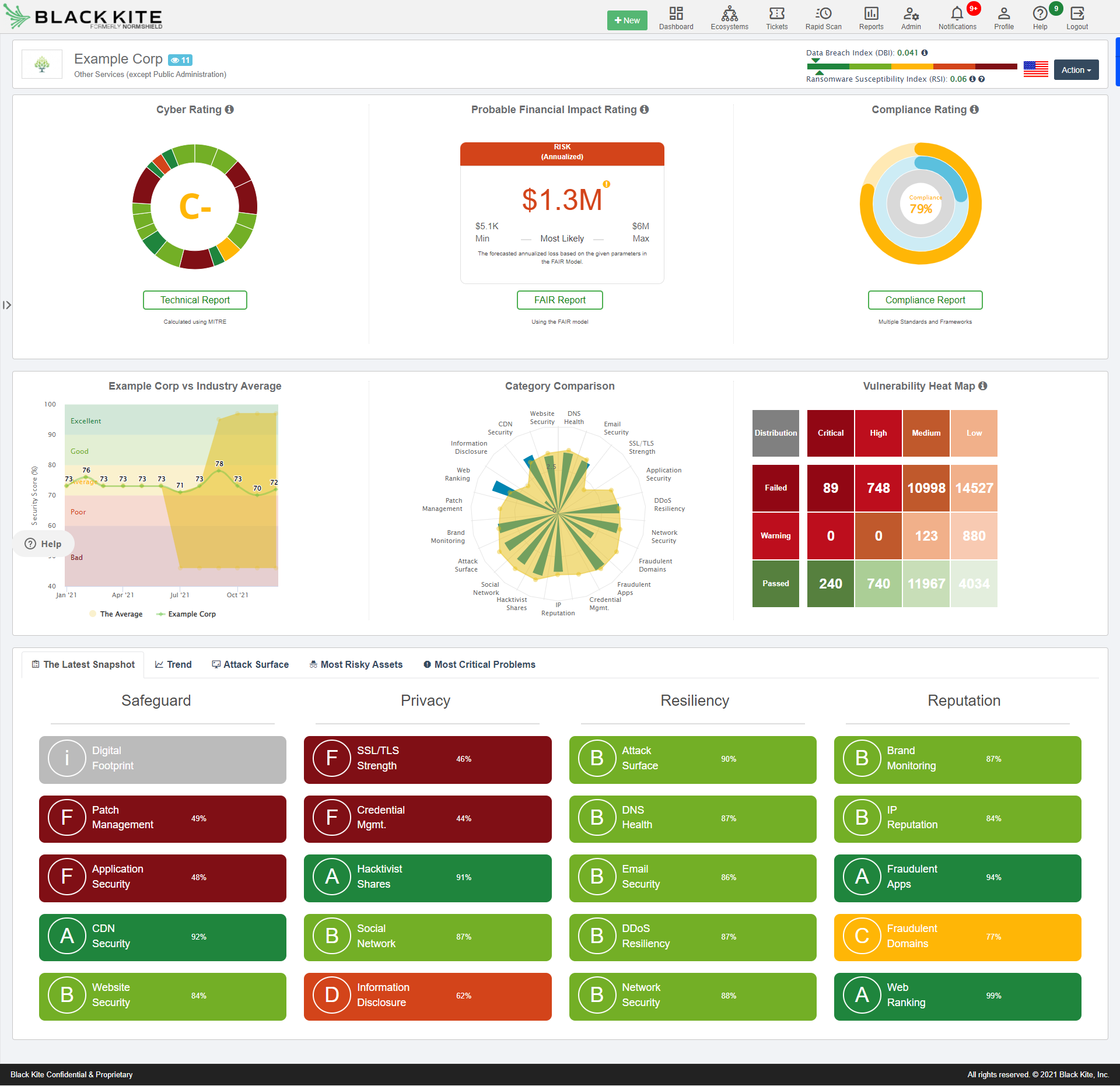
Sometimes there is an assumption that information security is about how good your security controls are, which is undoubtedly true; but how well a company’s digital infrastructure and assets have been configured and maintained, can play a hugely significant part in the likelihood of an attack being successful if the company is targeted.
Helping CISOs and cyber risk teams to clearly identify cyber risks, with clear and concise information about the root cause of the issue and how to fix and remediate them, is what we do.
Understanding and tracking changes to your Digital Footprint
It all starts with the Digital Footprint. This is an exhaustive and dynamically updated itinerary of all externally facing assets that make up your Attack Surface. Some companies already track their digital footprints, others do not, while others incorrectly believe that they are aware of all digital assets within the scope of their responsibility. We will ensure that all of your digital assets are identified and constantly updated.
Poor configurations and patch management
For most companies, IT assets and infrastructure will have been added in an ad hoc manner over a period of time. Some of these assets may have been poorly configured from a security perspective. Others require constant attention to retune and to patch vulnerabilities. We help you to identify key misconfigurations in your infrastructure and to create a risk-based remediation fix list, focusing on the most critical risks to address first.
Ransomware risk
Ransomware remains one of the top cyber risks to a business and senior executives and the Board need to clearly understand the likelihood of a Ransomware attack on your business or on one of your critical vendors.
 We work with you to constantly monitor over 200 key Ransomware risk indicators to produce a Ransomware susceptibility score – and full technical details on how to fix and remediate assets that contribute to this risk.
We work with you to constantly monitor over 200 key Ransomware risk indicators to produce a Ransomware susceptibility score – and full technical details on how to fix and remediate assets that contribute to this risk.
Fraudulent sites, apps and leaked credentials
Leading EDR vendors now believe that endpoint defences are now generally so good that attackers are switching their focus on harvesting user credentials as a way to bypass defences. Setting up fraudulent (Phishing) websites and apps, social engineering and direct acquisition of user credentials are all techniques that are commonly used. Elasticito helps you to identify where user credential risks are occurring and can advise on ways to mitigate and reduce this risk.
Our strategic partnership with SANS Security Awareness to change user behaviours and to promote a security-considered culture within the organisation, plays a significant part in this.
Quantifying cyber risk
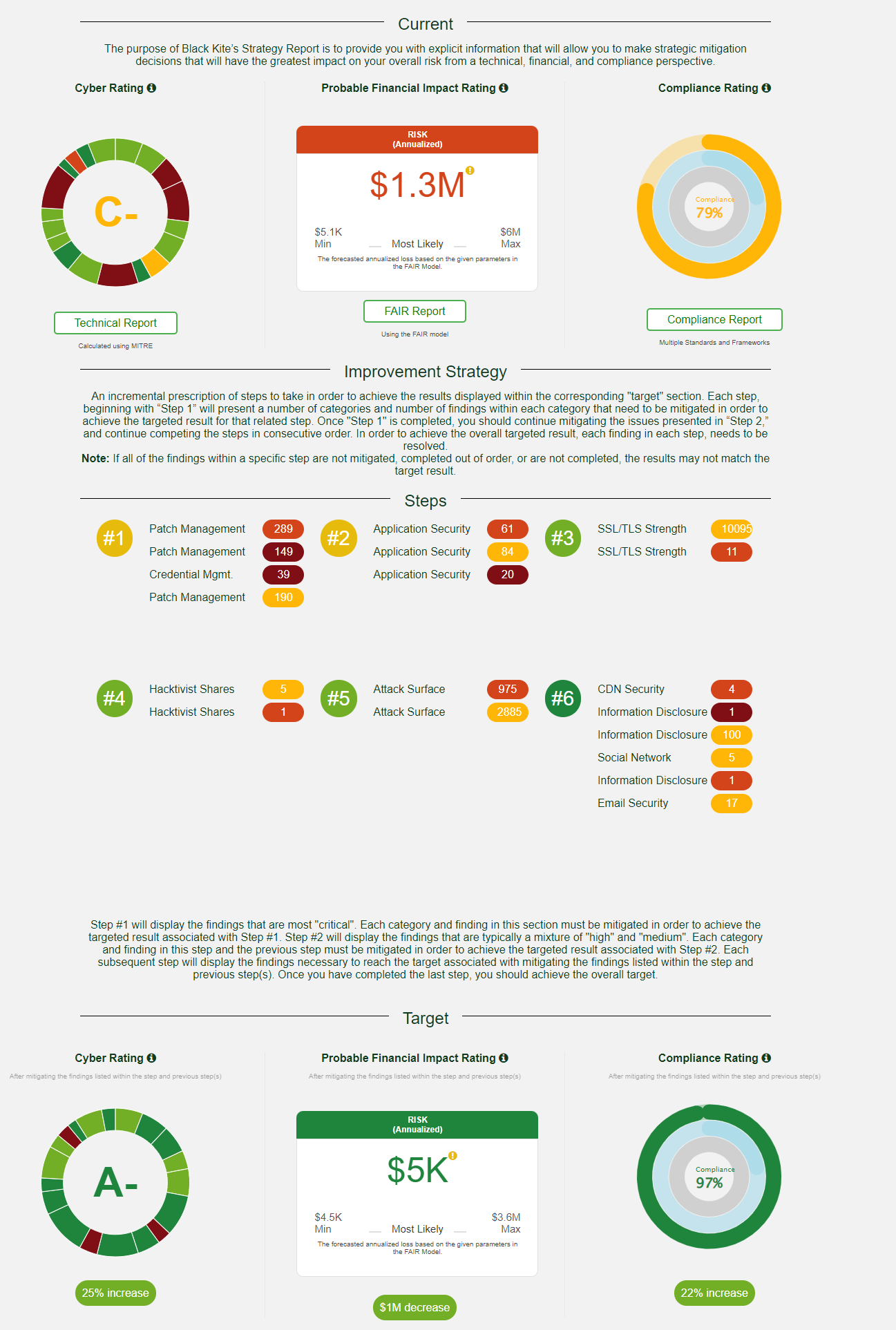
Presenting a summary of your company’s cyber risk posture to the Board can be challenging for CISOs and cyber risk professionals. First up, it is complex and senior executives may not understand the nature or impact of the risks that are being presented to them.
That is why it is important to be able to quantify cyber risk in financial terms. Elasticito can help you to quantify your own company’s cyber risk posture, but also the financial risk that third parties bring to your business. Find out more here.
Better preparation for regulatory audits and external security assessments
If preparing for PCI, ISO 27001 or other regulatory and security audits means having to down tools to focus on these activities, we can help. Our automated tools and expert advisory services will clearly show you how you are tracking against 10+ industry and regulatory frameworks, like ISO 27001, NIST 800-53, NIST CSF, GDPR, PCI DSS, Shared Assessments Standard Information Gathering (SIG) assessment and others.
Elasticito offers a range of managed services offerings to help you analyse and monitor cyber risks.
Contact us to get a free cyber risk assessment report for your company and to discuss how we can help.