3 Steps to Holistic Third-Party Risk Management
As businesses increasingly rely on third-party organisations to provide goods and services, it’s important for CISOs and risk teams to understand the potential risks involved. If data sharing or interaction with customer data is required, the organisation’s exposure to risk can significantly increase. By keeping a close eye on third-party activity, CISOs can help protect their company’s data and reputation. Here are 3 steps to holistic third-party risk management.

Definition
Third-party risk management (TPRM) is a newer term that describes vendor risk management, vendor management, supply chain risk management or supplier risk management.
TPRM is a focused subset of enterprise risk management that identifies and reduces risks when third parties are leveraged to perform specific tasks. These entities include vendors, suppliers, partners, contractors, and service providers. TPRM is all about understanding, monitoring and managing the risks that come from interacting with external organisations. A good TPRM programme should help an organisation understand what safeguards are necessary to protect its data (including customer and vendor data), and ensure that these measures are implemented by the organisation or its third parties – or both.
Third-party risk management is a complex and challenging endeavour for organisations, given the sheer number of suppliers they have to onboard and manage (60% of organisations work with more than 1,000 third parties). The diverse and unique requirements of different businesses can add to this complexity. For example, in the oil and gas industry, the digitisation of manufacturing companies is occurring at a rapid pace, which increases the difficulty of managing third-party risk within their supply chain.
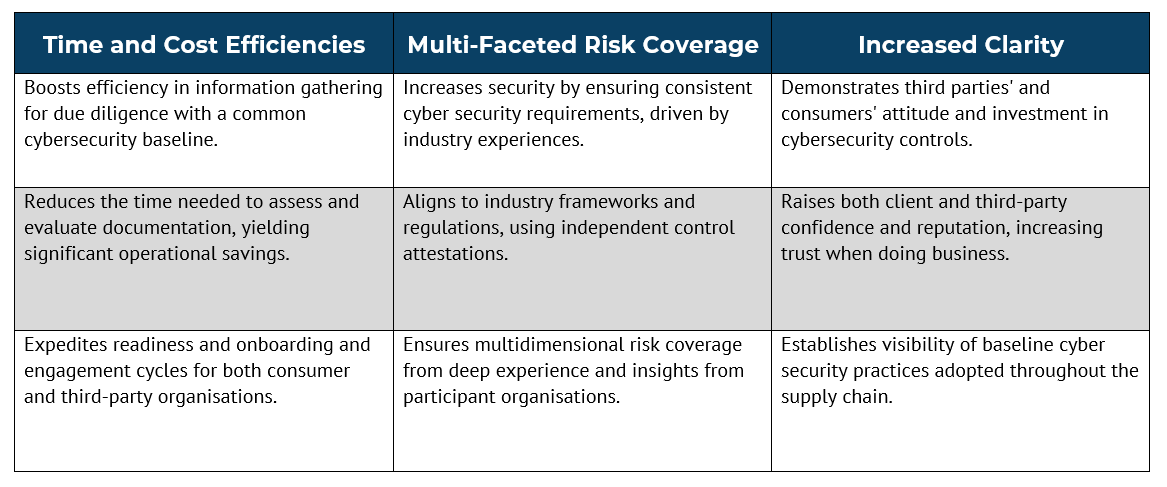
Benefits of a Holistic Approach to Risk Management
Collaborative action and a holistic approach across stakeholders in the supply chain will provide multiple benefits to organisations. The benefits of a holistic approach to risk management are:
- Time and cost efficiencies
- Multi-faceted risk coverage
- Increased clarity
Adapted from: World Economic Forum
3 Steps to Holistic Third-Party Risk Management
As cyberattacks become more sophisticated and costly, organisations must do more to protect their systems from third-party threats. In today’s interconnected world, it is crucial for supply chain stakeholders to partner with TPRM professionals to take a holistic approach to managing emerging risks, streamlining processes and increasing transparency throughout the organisation. By working together, we can create a safer, more efficient and more transparent supply chain that benefits everyone involved.
Despite some progress in this area, many companies are still not doing enough to secure their data and systems. With the rapid pace of change in the cyber threat landscape, organisations cannot afford to wait any longer to take action. They need to implement comprehensive security measures to safeguard their networks and data against increasingly sophisticated attacks.
So how can organisations create a highly effective, better-managed TPRM program? How can you reduce the risk that your vendors pose? Elasticito has compiled “3 steps to holistic third-party risk management” to help you do just that.
Step 1: Vendor Categorisation
It is important to understand who your vendors are, what they do, and how dependent you are on them in order to effectively manage third-party risks. Knowing your suppliers’ roles and responsibilities is key to identifying the risks and vulnerabilities they may pose, whether they be upstream, midstream, or downstream.
In particular, it is important to focus on vendors and third parties that:
- you share data with
- have access to your company’s network
- have access to your company’s offices and/or facilities.
Types of risks that vendors can cause to your company:
- Strategic risks
- Industrial risks
- Reputational risks
- Geographical risks
- Credit risks
- Transactional risks
- Operational risks
- Compliance risks
There are many vendors your company might work with that could pose various risks. By categorising each vendor’s potential risks, you can better understand what actions need to be taken to remediate these risks. The risk profile of each vendor can be defined through the process of risk identification and integration, risk classification and analysis, control evaluation, and risk reporting and treatment. This will help you mitigate any risks posed by vendors, depending on the criticality of the vendor and the type of the risk.
Step 2: Deciding What You’ll Be Evaluating
As your organisation looks to bring in new suppliers, products, and services, it is important to have a robust evaluation approach in place that can identify and assess the level of risk that each may bring. This evaluation should take into account different criteria and methods, such as scoring ratings, shared assessments, industry certifications, and internal assessments. By taking all of these factors into consideration, you can make more informed decisions about which suppliers, products, and services are best suited for your organisation.
When it comes to risk, there are two main ways to classify it – either according to the relationship you have with the vendor, or according to the type of data it handles. When working with third-party vendors, it is essential to agree on how data will be stored and used during and after the relationship, in order to avoid any potential damage to your company.
Types of third-party relationships:
- Infrastructure Only – The vendor provides only main infrastructure, such as servers and network devices.
- Managed Applications – The vendor gains some control over the installation, maintenance, and support of the applications.
- All Data – The vendor maintains control over both infrastructure and applications. The vendor can also perform disaster recovery such as backup and data recovery features.
Assessing vendors involves a number of steps that your company must follow to get rid of potential problems in the future. The first stage of vendor management usually involves creating and maintaining questionnaires and checklists. These are organised into hierarchies so that certain sections can be assigned to multiple vendors. The purpose of these checklists is to either conduct a full audit of the vendor or assess specific risks. This all depends on the scope of the risk assessment. Assessing vendors via spreadsheets and emails, however, is a very time-consuming, convoluted and tedious process.
There are world class TPRM tools and accompanying services available which can transform this process by providing an end-to-end cyber risk assessment and governance platform that replaces spreadsheet-based risk assessments with a slick and professional portal environment. Here third party users are invited to complete relevant dynamic risk questionnaires, where automated workflows keep tasks in order and reporting and insights are generated automatically by the system.
Step 3: Continuous Monitoring and Alerting
It is important to continuously monitor all third parties for potential risks. This can be done by ensuring that there are mutually agreed-upon cybersecurity contractual terms and conditions in place. Additionally, it is necessary to assess if additional terms are needed based on internal inherent risk approaches or segmentation criteria. Engaging with subject matter experts who are familiar with risks, as well as legal departments, throughout the negotiation process is key.
It is important to periodically use questionnaires, surveys, and audits to assess the vendor’s compliance requirements and security controls, or use a technologically advanced tool such as Black Kite. Black Kite provides intelligence from a technical, financial and compliance perspective; eliminating false positives and ensuring a truly holistic approach to TPRM.
Ongoing monitoring and detection of compliance and security issues in real time is critical to understanding your third party risk landscape. By constantly evaluating this data, you can make informed decisions about which risks to take and how to mitigate them. Most organisations understand its importance, especially amidst a series of headline-grabbing supply chain attacks such as Kaseya or SolarWinds. However, for some, it can be challenging to decide where to start building and scaling an end-to-end TPRM program that truly monitors risk on an ongoing basis.
Impact of Breaches Caused by Third-Parties
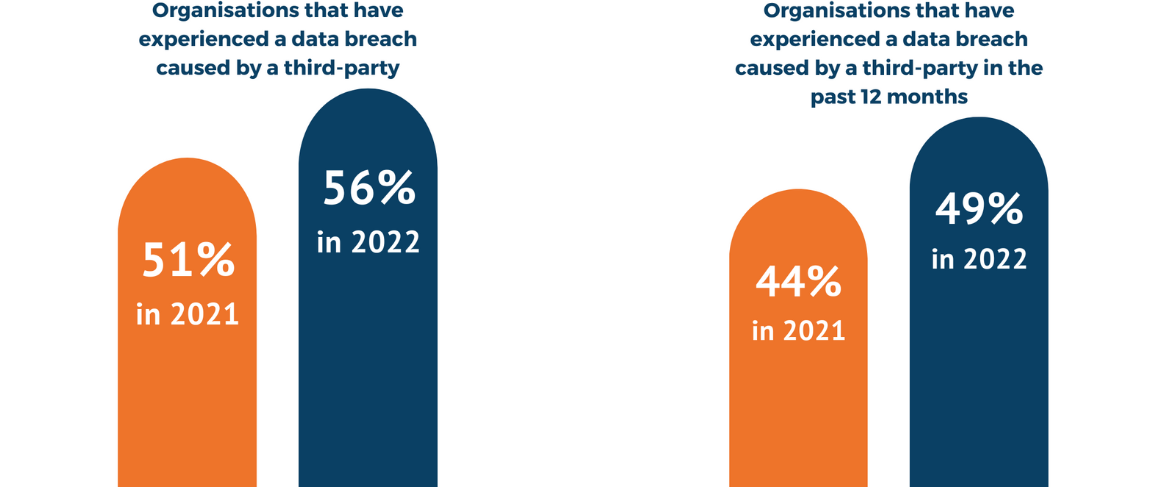
Breaches caused by third parties can have truly devastating consequences for businesses and economies. In 2022, the average cost of a data breach has reached a record high of US$4.35 million, according to the 2022 cost of a data breach report by IBM and the Ponemon Institute. In the current economic climate, businesses will struggle to survive such a loss.
In fact, third-party data breaches have been responsible for more than 51% of all data breaches over the last two years. These breaches can occur directly through a third party, or indirectly through a breach of the third party that then provides access to the primary contracting organisation.
Adapted from: SecureLink-Ponemon Report 2022
In a hyper-connected world, it is essential for supply chain stakeholders to collaborate and align their third-party risk governance practices. A collaborative, aligned and holistic approach will help streamline the process and mitigate future risks, while delivering time and cost efficiencies, multi-faceted risk coverage and increased clarity.
Summary
Third-party vendors can be a great asset to any organisation, but it is important to be aware of the risks involved in working with them. Different vendors can present different types of risk, such as strategic risk, compliance risk, operational risk, etc. Ignoring these risks can lead to data breaches or other compliance issues.
To avoid these problems, companies should take some proactive measures into account when partnering with or outsourcing services to third-party vendors. These measures include (1) conducting vendor categorisation, (2) deciding what you’ll be evaluating and (3) continuous monitoring and alerting. In addition, effective vendor selection and management is also essential. Doing these things can help organisations prevent data breaches and minimise the risks associated with third-party vendors.
For more information or obligation-free advice regarding updating or aligning your third-party risk management program, contact the team at Elasticito.
