4 Tips for a successful cyber threat intelligence program
The information security threat landscape is constantly evolving, becoming more complex and in many cases, overpowering the security environment. The number of successful hacker attacks each day is increasing. Cyber criminals are continually developing new ways to disrupt organisations via cyberextortion, supply chain hacks, and other cunning tactics. An organisation’s security team must be more proactive in planning for and dealing with these threats. One of the ways to do this is to make use of cyber threat intelligence (CTI). Here’s how to get the most from your CTI program.

What is cyber threat intelligence?
In essence, cyber threat intelligence can identify and analyse cyber threats to your organisation. It’s what becomes of data after it’s been gathered, processed and analysed. CTI relies heavily on analysis: sifting through large amounts of data to spot realistic problems and then deploying suitable solutions specific to the relevant issue uncovered. CTI needs to be accurate, actionable, relevant and timely to your specific organisation or vertical.
The definition of threat intelligence is often confused with other cyber security terms, such as “threat data”. Threat data is a list of possible threats a computer system may encounter. Threat intelligence is current and relevant information about those threats. Typically, threat intelligence is raw data collected from multiple sources and methods such as tools, blogs, dark web, news reports, and social media commentary (Figure 1). The more channels you have that provide information about potential threats, the more useful the information will be. Threat intelligence is a vital part of any healthy cybersecurity ecosystem.
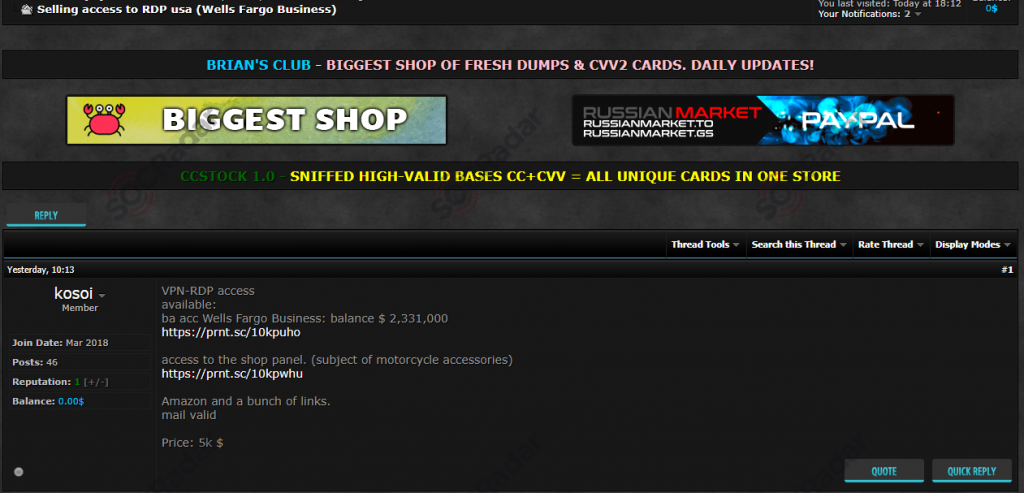
Figure 1: Dedicated dark web shops, such as this vendor of VPN-RDP access instances, can uncover indications that clients’ infrastructure has been compromised (Source: SOCradar).
The CTI lifecycle
Instead of a linear process, threat intelligence in the digital world works in a circular process called the “cyber threat intelligence lifecycle”, which operates in a cycle because new questions and knowledge gaps could emerge during the process which may generate new requirements (Figure 2).

Figure 2: The CTI Lifecycle (Adapted from: SOCradar).
This CTI lifecycle creates a feedback loop which makes it possible to understand and constantly analyse an organisation’s cyber attack threat level. This enables the security ecosystem to proactively adapt and optimise its line of defense.
By identifying and analysing threats, CTI spots patterns used by hackers and helps businesses put security measures in place to safeguard against future attacks. With a well-structured CTI program in place, your company can spot cyberthreats and keep data breaches from releasing sensitive information.
Four tips for a successful CTI program
Cyber security is an intelligence-led approach. Without in-depth knowledge of threats, organisations face a risk of being defenseless against increasingly sophisticated attacks, and are at greater risk of recurring attacks. Just like other forms of security, cyber security needs to be managed intelligently with a thorough understanding of business risk then implemented strategically. Here are four tips for a successful CTI program:
- Operationalise your CTI program
Threat intelligence information requires centralised analysis. Analysts need to compare different feeds of cyber threat intelligence and produce workstreams that can block threats before they happen. Operationalisation occurs only when security analytics produce clear-cut results without diverting too much time or resources. All cyber threat intelligence records are compared whereafter runbooks are created to turn malicious IoC’s into blocking rules on firewalls, web gateways, endpoints, email security filters, etc. SOAR tools are often used by organisations to help automate this process.
- Analyse the CTI findings
For a business to succeed, it must continuously and rigorously analyse its strengths, weaknesses and possible threats. Organisations should keep a keen eye on trends in open source threat feeds and dark web chatter as well as social media posts and blogs to better understand ways that competitors could be mounting a digital attack against them. Beyond controls and audits, these organisations want to understand who is attacking them and the techniques, tactics, and procedures that are being used to gain unauthorised access. This intelligence is collected, transmitted for analysis, processed, stored for future use, and then finally made available to the organisation’s IT department for security oversight. Analysis is very focused on adversaries and campaigns that pose a direct risk to organisations. Today’s CTI programs are very different than they used to be. They’re governed by strong processes and regulations, requiring formal approach, documentation, and the use of purpose-built platforms. These systems enable businesses to sort through massive CTI volumes, more easily analyse collected threat intel, and compare it to internal behavior. In addition, they can give you the power to investigate and contain new threats in near real-time.
- Sharing and networking with others in the industry
Leading organisations participate in industry ISACs (Information Sharing and Analysis Centre), Meetups, LinkedIn groups and local communities as CTI providers and consumers. Successful threat analysts have strong personal networks they regularly communicate with on an informal basis. Think about what you have in your personal network: family, friends, alumni, other professionals, etc. Every single person you interact with on any level has something to offer. When vulnerability research is part of an organisation’s regular operations, the best place for information sharing is the same place people have access – their personal networks. Leading companies must be active participants in ISACs and local communities. Local and global networks are crucial to collaboration, and for leading cybersecurity professionals to stay up-to-date with the latest threat intelligence. There’s no replacement for the knowledge of peers who can pass along information when they feel it’s appropriate. Such connections should be used, not abandoned. Because threat actors get smarter day-by-day, cyber security experts who share tactics the have come across within the community effectively create a collective knowledge pool to dip into when facing a threat.
- Maintain historical security data records
The time between discovery and remediation can be measured in hours, days, or even years. It is a cat-and-mouse game where security analysts have to keep an eye out for new malicious campaigns. Security researchers and threat hunters have been required to crawl security telemetry logs to find the proverbial “needle in the haystack”. Threat analysis is a critical part of security operations today. It requires maintaining historical records of structured security data in Security Information and Event Management (SIEM) solutions.
Common indicators of compromise
The Covid 19 pandemic has opened the cyber attack floodgates across the globe. Organisations are now, more than ever, under mounting pressure to effectively manage their cyber security vulnerabilities. CTI feeds can greatly assist in this process by identifying indicators of compromise (IoC) and recommending actions to prevent attack. Common indicators of compromise include:
- Domain names, URL’s and IP addresses. For example, malware targeting an internal host that is communicating with a threat actor.
- Links and attachments, email addresses and subjects. For example, a phishing attempt that requires a user to click on a link or attachment which initiates a malicious command.
- DLL’s, file names and registry keys. For example, an attack from an external host that is already infected.
The world is full of unknowns. The greatest risk? The unidentified threat. In today’s world, hackers are constantly finding new ways to threaten your online vulnerabilities. Using a tool that unpacks threats is the best way to ensure your organisation does not fall victim to these unknown criminals. By using threat intelligence, you can gain valuable knowledge and insights pertaining to cyber threats and build effective ways of defending against them.
Need more information?
While the allure of “cyber risk intel” is compelling, it is important to understand how it operates so you can choose the right cyber risk tools and solutions to protect your organisation.
For organisations seeking a holistic approach to cyber threat intelligence Elasticito can provide a comprehensive solution that enables businesses to focus on putting intelligence to work rather than collecting, processing, and deploying their own threat intelligence.
Contact the team for more information.
