Making the case for Security Assessment Questionnaire Response Automation
Business partnerships require trust – without it, success is very difficult to attain. In the current business landscape, however, it’s increasingly difficult to tell whether a vendor is trustworthy and deserving of that trust. As information technology becomes more advanced, so do the ways in which trust can be broken. Today, the potential for intentional or unintentional breakage of it has increased multifold.
Assessing security risk with questionnaires is one method to effectively understand the security risk that a vendor may pose to the business, particularly if you entrust them with your data. If you are reading this article, you’ve more than likely handled your fair share of security assessment questionnaires. Like us, you are probably frustrated by the entire process too. We would like to make the case for automated security questionnaires in the article below.

The traditional approach to security questionnaires
In 2020, the global average cost of a data breach was $3.86 million, according to Ponemon’s Cost of a Data Breach Report. The report also notes that should a third party cause the data breach, the cost will increase — by more than $370,000. It is no wonder that in the wake of GDPR and large data breaches, businesses require due diligence from their third party vendors, usually in the form of security questionnaires.
Security questionnaires are used to help determine whether vendor security practices meet due diligence. That way, your business can decide whether or not to entrust them with your data. Notoriously annoying to complete and administer, security questionnaires require good planning to extract useful insights from your vendor risk management plan. Often mandated by contracts and industry regulations, it seems there is no way around the tedious process of filling out lengthy questionnaires.
A security questionnaire assesses your technology systems, physical security and policies. As illustrated in Figure 1, an overarching security assessment plan will often involve the following entities: assessment, review, identify risks, remediation and risk register:
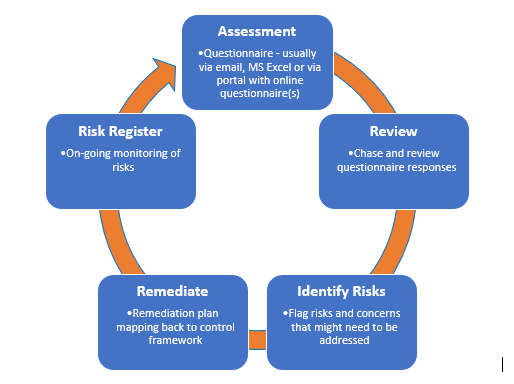
Figure 1: Vendor Security Assessment Process
The traditional approach to security questionnaires is manual and inefficient. Businesses send out the security questionnaires in the form of spreadsheets or documents. Often supporting documents must also be submitted in hardcopy format. Responding to security questionnaires takes time, energy and resources. Frequently, security questionnaire content is stored on systems like Google Drive, Sharepoint or other databases. The security questionnaire response process may be managed via Excel or a project management tool. Respondents will have to search through a number of individual documents to find answers, having to manually extract the content repeatedly. Sifting through the documentation to understand risk posture and setting up remediation plans is a gargantuan task – imagine the auditing process for a thousand or more vendors.
On the other hand, an automated platform provides a collaborative environment where questions can be clarified, evidence viewed and remediation discussed.
The modern approach to security questionnaires
Information security risks assessment is the first step towards finding and correcting vulnerabilities that could lead to an information breach. It is a crucial tool in creating a cost-benefit analysis for selecting appropriate controls based on risk and business needs. Using an automated information security risk assessment tool will:
- simplify data collection
- aid in identifying current risks
- evaluate risk severity
- predict possible future events
- automate follow-ups
- enable standardisation
Through automation, the risk assessment process will be greatly sped up. Whereas manual assessment requires 4 weeks per entity to be conducted, automation reduces this down to only one hour (Figure 2, below). Also illustrated is the significant cost and resource reduction automation provides over the traditional, manual process.

Figure 2: Time, cost and resource comparison of manual vs automated cyber risk assessment
The Black Kite solution to security questionnaires
Most organisations have security policy documents that they maintain for audit and other purposes. An organisation’s cyber security policy outlines the guidelines for transferring company data, accessing private systems and the use of company issued devices. These documents generally reflect a true and realistic view of the state of security policies, controls and processes internally. It is these documents that are used to automatically answer vendor security questionnaires using Black Kite’s patent pending Universal Parsing Engine. “With Black Kite, you can transform a week’s work into one hour”, says Elasticito CEO Ronan Lavelle.
Figure 3 clearly illustrates the opportunities to automate the Vendor Cyber Risk Management Lifecycle (VCRM). With an effective and reliable automated security system, your organisation’s manual effort will be reduced and the speed of internal processes increased. Using Black Kite’s Strategy Report, you can easily share questionnaires with vendors. Vendors can complete the questions and the answers can then be mapped to regulations and frameworks in the system.
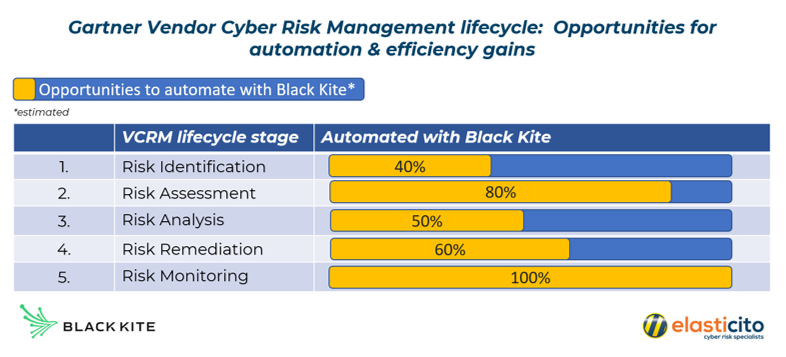
Figure 3: Opportunities for automation in the VCRM lifecycle stages.
Cyber security risk assessments have long been a function of IT security professionals. Increased awareness and a growing need for industry-wide compliance have driven the importance of cyber risk assessment automation as an integrated and integral part of an overall information security program. CISO’s can use tools such as Black Kite to gain greater visibility into the risk posture of their organisation, determine how threats and vulnerabilities may be impacting business operations, and determine how best to mitigate those risks to meet compliance and regulatory requirements.
Black Kite’s rating technology uses OSINT to compare vendor cybersecurity to industry standards. As illustrated in Figure 4, below, Black Kite assigns a probable financial impact rating to your organisation’s risk posture using OpenFair.
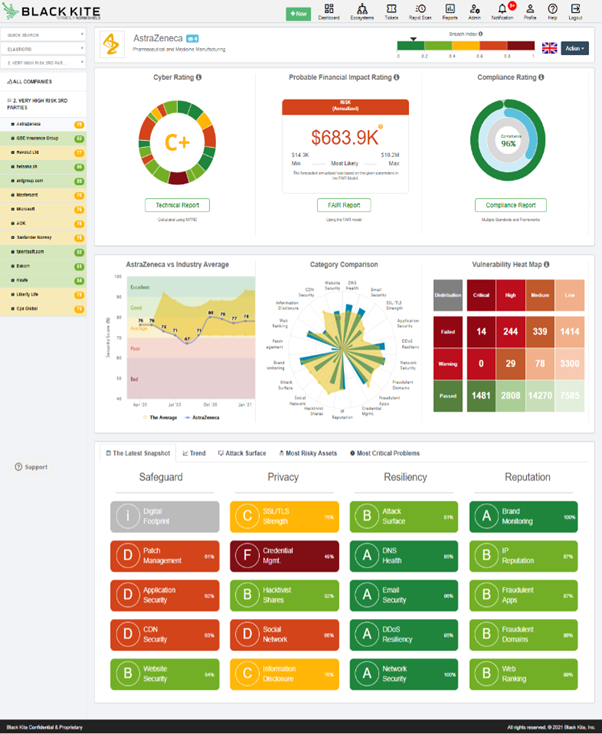
Figure 4: Black Kite Dashboard
If the majority of your employees’ time is spent answering security questionnaires, it’s time to automate your process. This will free up your security team to do what they do best: securing your business. Automation takes over when your security team can’t find the most accurate answer to a customer’s question on a spreadsheet. An automated database uses artificial intelligence, machine learning, and auto-matching technology to read thousands of security questionnaires and provide an accurate answer in seconds — saving your business hours (and money) per customer.
Concerned about how automation would work when you’re receiving questionnaires in various formats, such as MS Word, Excel spreadsheets and via online portals? Intelligent assessment platforms on the market today will work alongside any type of questionnaire you receive.
Conclusion
A security assessment solution such as Black Kite will:
- increase the efficiency of conducting third-party risk assessments
- reduce the time to remediation
- reduce the amount of time that exploitable vulnerabilities go unaddressed in an environment
The key to implementing successful automation technology is choosing a product that integrates with your organisations existing processes and can effectively manage your third parties and vendors.
Contact the Elasticito team to discuss how to turn your organisations focus on admin into a focus on analysis.
