Understanding Cyber Risk Exposure for Vendors in Russia & Ukraine
It was only 60 years ago when the world feared a global nuclear war. Fortunately, we made it through that period. But with geopolitical tensions at an all-time high, the risk of a devastating global cyber war is becoming more and more likely. This is why each of us needs to do our part to reduce cyber risk. Understanding cyber risk exposure for vendors in Russia and Ukraine should be a priority for all businesses with vendors in those countries.

Recently, the United States (US) and other countries imposed sanctions on Russia for its invasion of Ukraine. These sanctions have sparked a considerable amount of concern, especially surrounding the issue of cyber attacks on US organisations and those based in allied countries. These are uncertain times, but many experts predict that the attacks will be wide-ranging. They’ll involve ransomware and disk wipers, phishing, disinformation campaigns and false information, which might even be state-sponsored.
Cyber War Capabilities & Attack Methods
CTO of Elasticito, Andrew Brown explains: “One of the most prevalent cyber attacks is ransomware, where hackers extort money from victims who have had their files or computer network compromised. In recent years, the use of ransomware for extortion has become a security issue of serious concern.” To corroborate, Chris Krebs recently said: “… every organisation could be affected. Or should at least plan to be prepared, because we’ve seen ransomware actors in the past not necessarily be as strategic in their targeting, instead being incredibly opportunistic”.
Microsoft Threat Intelligence Center (MSTIC) and other threat intelligence sources have disclosed that the WhisperGate destructive malware is actively being used to target organisations in Ukraine and beyond. The HermeticWiper malware is also in active use, which results in boot failure and renders systems inoperable.
In the most recent advisory, Cyber Security and Infrastructure Security Agency (CISA) and the FBI also noted that “destructive malware may use popular communication tools to spread, including worms sent through email and instant messages, Trojan horses dropped from websites, and virus-infected files downloaded from peer-to-peer connections. Malware seeks to exploit existing vulnerabilities on systems for quiet and easy access,” the advisory stated.
Also, UK’s National Cyber Security Centre (NCSC) and CISA have released details about a new malware targeting network devices, which they attributed to Sandworm (aka BlackEnergy), a threat actor that those agencies have previously attributed to the Russian GRU’s Main Centre for Special Technologies GTsST.
The threat actor has so far primarily deployed Cyclops Blink to WatchGuard (firewall) devices, but it is likely that Sandworm would be capable of compiling the malware for other architectures and firmware. The malware collects device information, sends it to a command and control server, and is capable of downloading and executing files, as well as getting additional modules at a later date. The most interesting thing about this malware is its persistence mechanism; the devices’ legitimate device firmware update process:

Source: Help Net Security
What All Organisations Should Do
The CISA, FBI, NSA and other security organisations are encouraging all businesses to take a proactive stance against cyber threats. They urge defenders of critical infrastructure to be aware of the dangers and to use threat hunting to stay proactive. Additionally, they urge these businesses to implement the following recommendations to reduce the risk of being compromised. These recommendations will help organisations reduce the risk of severe business degradation.
- Be prepared. Confirm reporting processes and minimise personnel gaps in IT/OT security coverage. Create, maintain, and exercise a cyber incident response plan, resilience plan, and continuity of operations plan so that critical functions and operations can be kept running if technology systems are disrupted or need to be taken offline.
- Enhance your organisation’s cyber posture. Follow best practices for identity and access management, protective controls and architecture, and vulnerability and configuration management.
- Increase organisational vigilance. Stay current on reporting on these threats.

Source: CISA
How Black Kite and Elasticito Can Help
In today’s interconnected world, a global conflict can affect us all, even if we don’t realise it. If you have any assets in Ukraine or Russia, or conduct business with organisations that do, you need to be prepared for potential disruption. It is crucial to have contingency and redundancy plans ready as the conflict escalates. Alternatively, you can conduct a survey of your vendors and clarify their risk exposure to Russia or use technology such as Black Kite.
Thanks to quick work from Black Kite’s development team, the platform now includes smart tags to detect vendors that might be affected by the ongoing Russia-Ukraine situation. This automated process is based on external attack surface detection through Open-Source Intelligence (OSINT) techniques. Vendor location and the location of IT assets are the primary detection data points.

Source: Black Kite
These new tags will help alert your customers and prospects to the impact of cyber incidents related to the Russia-Ukraine war on their vendor ecosystems. Even where vendors are not directly related to the two countries, organisations may still be impacted due to targeted 4th parties.
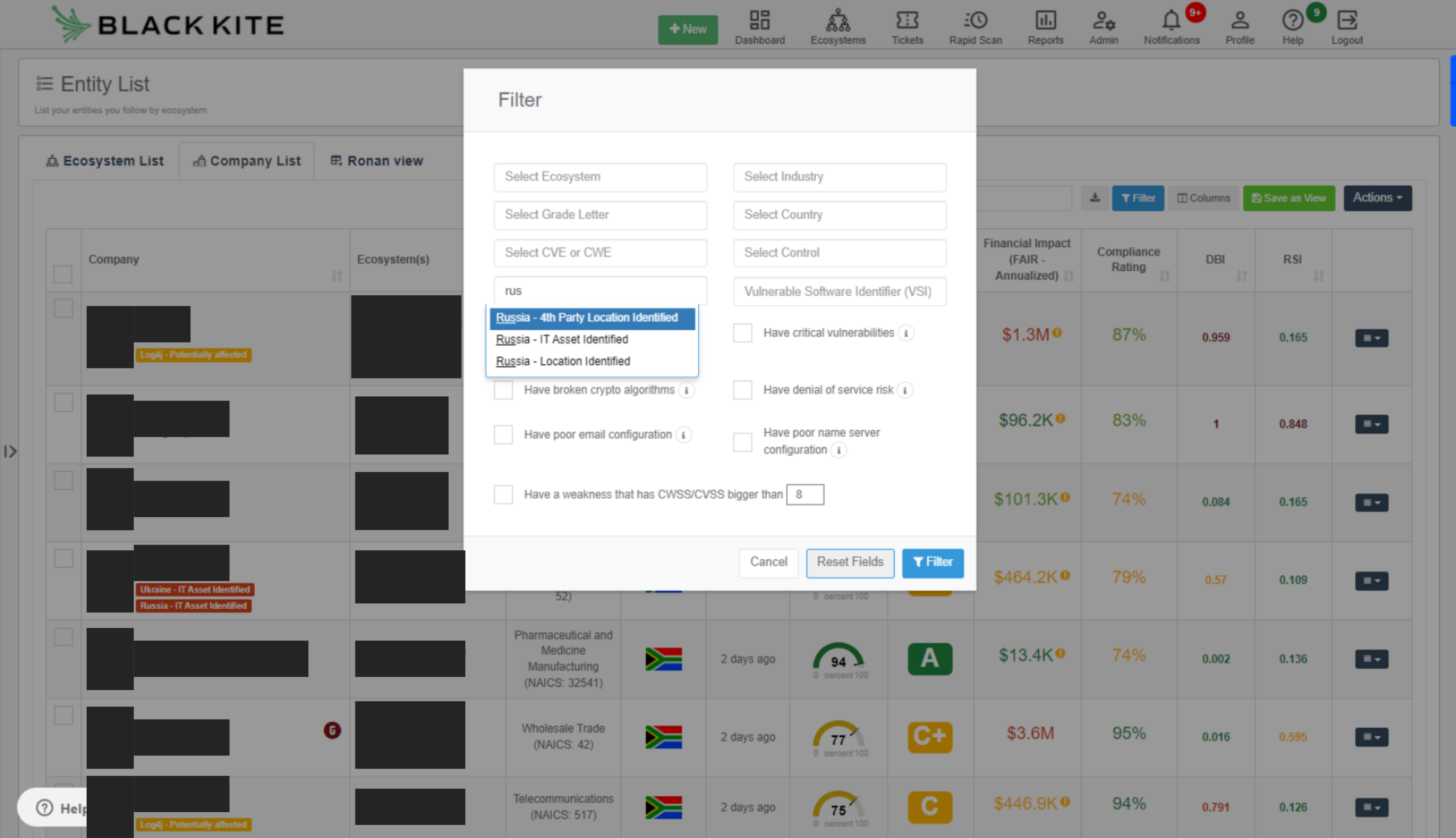
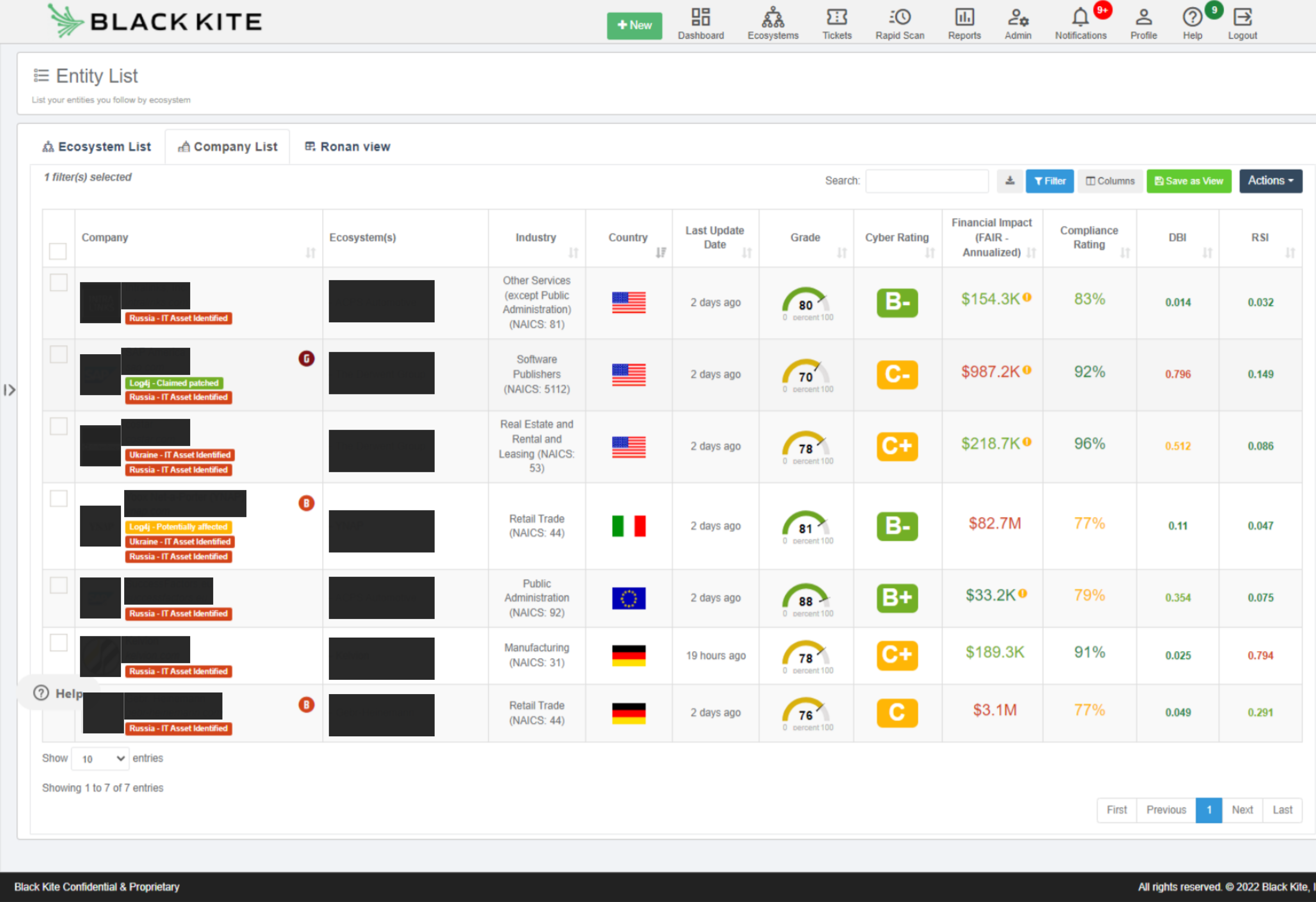
A component of Black Kite’s product offering is the insight it provides to assist customers in identifying vendor connections with other organisations. In other words, Black Kite allows it’s customers to identify the third party relationships of their third parties in order to have better awareness of impact to their supply chain. You can use this data to identify the customers that have plausible relationships with the previously identified organisations who have Ukraine- or Russia-based assets.
Set up a Black Kite demo with the Elasticito team here.
