How Do You Determine the Risk Impact of a Vendor?
Vendor risk assessment is an important part of business management. Vendor relationships can deliver value, but they also have risks. A vendor risk assessment is an important step when evaluating the risks your business may be taking with third-party vendors. Such a risk assessment can be about determining the risks your company is exposed to by a vendor’s products and services, or about the vendor potentially mishandling sensitive customer data or even interacting with customers. It’s important for a company to perform due diligence questionnaires and conduct third-party risk assessments when onboarding a new vendor. It’s also important for an organisation to continue performing periodic vendor risk assessments to assure its vendors are maintaining quality standards and don’t introduce any unexpected risks. This article will walk you through what the different types of vendors are and the risks associated with them. You’ll also learn some of the best practices for a vendor risk assessment and management team. The article will furthermore detail how to maximise diligence and monitoring in order to improve your company’s performance and mitigate risk. So how DO you determine the risk impact of a vendor?
What Is Vendor Risk Assessment?
Vendor Risk Assessment (VRA) is the process of evaluating potential risks or hazards associated with a vendor’s operations and products and its potential impact on your organisation. This type of assessment is also known as vendor risk review. You should perform a VRA for any company you use, but it’s especially important to do so for vendors who are producing products that are essential to the day-to-day operations of your business.
A third-party vendor risk assessment may be necessary when your organisation is faced with uncertain events. You determine the likelihood of these events, then identify and measure them. Potential risks include inaccurate and unreliable data, security breaches, and regulatory compliance. By performing a thorough due diligence on all vendors, you can mitigate those risks, provide a solid foundation for partnerships, and help maintain consistent operations.
Before doing business with any vendor, companies need to do a VRA. Every company should evaluate and screen all vendors to ensure smooth contact and assess any risks the vendor may impose on their business. A change in production, material supply, or processes can affect the supply chain and create disruptions in material flow or other risks. Understanding a vendor’s cyber security, data and privacy policies are essential to assessing their credibility.
Different Types of Vendor Risk Assessment Reviews
When developing a strategy for risk management, you should use vendor risk assessment reviews to predict and forecast the probabilities and impacts of potential hazards with organisations or businesses. Probability is a statistical dimension that describes how probable or realistic a potential event may be. The severity of the event is how painful it would be if it actually came true. The following graphic portrays the lifecycle of a vendor relationship:
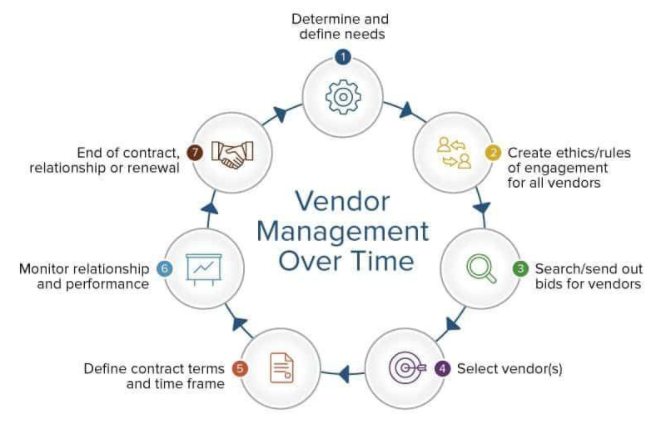
Source: Smartsheet
There’s a point where a risk becomes an event. This often gets confused, so we’ll say it clearly: a risk is not when an event has happened. A risk is a possible event that we haven’t seen happen yet. A risk becomes an event when it actually happens. Imagine that you have a project team member who says, ‘We’ve got risks!’ But what they actually mean is that you have a failure coming your way. The worst condition is when the event is a highly probable one with a high-impact severity.
Protecting data is a fundamental consideration in risk planning. By using a scale to rank vendors according to risk, you can more easily identify which partners need stricter security measures and monitoring. The figure below illustrates:
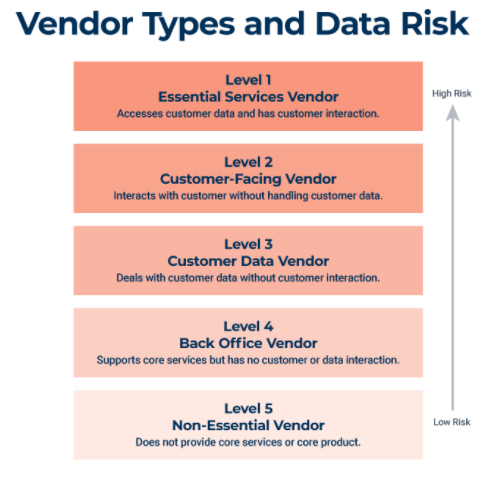
Source: Smartsheet
Let’s look at the categories of risk assessment and when you might want to use them:
- Qualitative Risk Assessments. Most risk assessments will fall under this category. When carrying out a qualitative assessment, the assessor will use their personal judgement to identify hazards, assess risks and plan control measures.
- Quantitative Risk Assessments. This type of risk assessment uses quantitative tools and techniques to measure the level of risks. A risk matrix may be used so that a value can be assigned to the likelihood and severity of risks. For example, you might use a 3×3 matrix.
- Generic Risk Assessments. Generic risk assessments assess the hazards and risks involved in work tasks and activities. They can be used in different locations and by different companies for activities that are the same/similar, so they’re often used as risk-assessment templates. Generic risk assessments often fulfil a variety of use cases, but they lack customisation. Outside of cyber security, an organisation might use these for managing contractor workers.
- Site-Specific Risk Assessments. These types of risk assessments are carried out for a specific activity in a specific location. Site-specific risk assessments are usually limited in scope and focused on a specific use case.
- Dynamic Risk Assessments. While most risk assessments focus on a moment in time, dynamic risk assessments focus on continuous evaluation and response.
How to Perform the Risk Assessment Process
Before you start the risk assessment process, make sure you’re ready for it. Buy-in from the entire organisation, including top executives, will help you stay on track. Set up a framework that you can use to monitor risk and to identify solutions to reduce risk. Apply the same criteria to all vendors, and adapt measures accordingly when outsourcing from third-party sources.
The risk assessment process involves understanding vendors, cataloguing them within your company, and creating reports that let you decide on whether or not to contract or renew them:
- Determine if the vendor is upstream or downstream.
- Classify vendors by how critical they are to the business.
- Develop a risk profile.
Risk assessments usually take the form of questions with answers applied to a vendor management risk assessment matrix grid such as the one below:
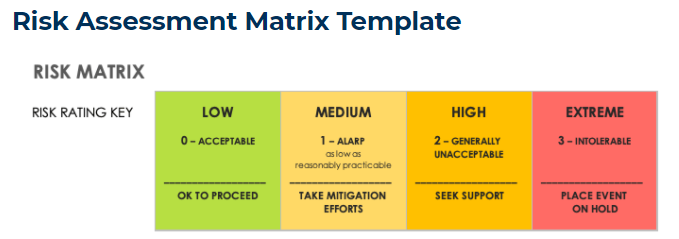

Source: Smartsheet
Using this simple methodology, a high-level calculation of cyber risk in an IT infrastructure can be developed:
Cyber risk = Threat x Vulnerability x Information Value
What Is Vendor Risk Management Software?
Vendor risk management software helps organisations automate their vendor risk management program. VRM software is able to collect and dynamically manage data about vendors that could lead to breaches or non-compliance in order to better protect companies from data loss or regulatory noncompliance.
For example, supply chain professionals manage due diligence questionnaires by using software. The software will distribute, collect, analyse, and store the results with the added benefit of providing notifications for any red flags detected. And as for compliance officers, third party risk management software is a great help with the management of government regulations like GDPR or HIPAA.
At Elasticito, we believe that compliance and audit-readiness are the keys to any organisation’s long-term success. That’s why we strive to provide you with a single source of truth, so you know your policies and procedures are up-to-date. We also offer workflow management features that allow you to easily track crucial information and create audit trails. In addition, our insightful reporting and dashboards provide visibility to gaps and high-risk areas of your company.
Discover a powerful yet simplified solution to risk and compliance.
Time is money and all the tedious work of monitoring suppliers can be a really big waste of time. Managing your suppliers takes the hassle out of risk management. Choose a provider with continuous monitoring capabilities to assure that you are always on top of the compliance hygiene of your third parties. In addition, look for a provider that provides templates, streamlines workflows and provides invaluable insights into the things you may not have been able to see on your own.
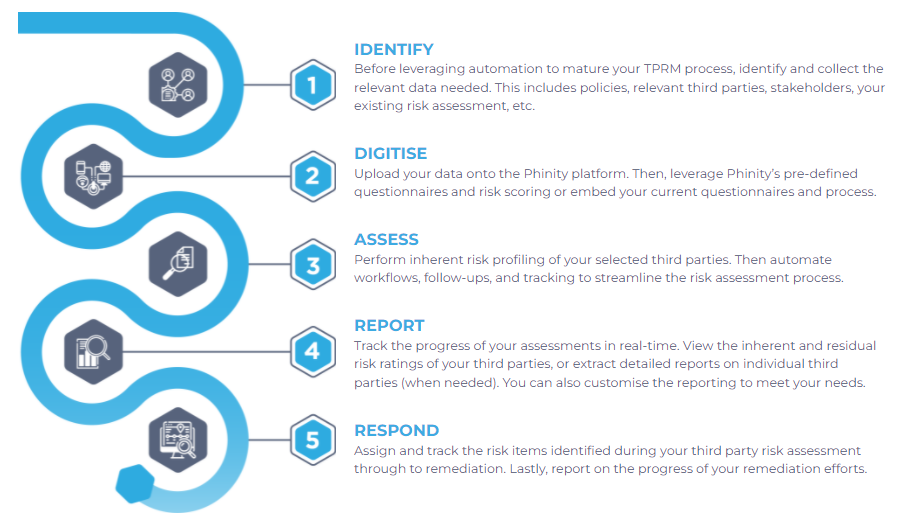
Source: Phinity
With risk management software such as those from Phinity (process illustrated in the figure above), you can automate supplier risk management. Risk management is time-consuming and tedious, which means you spend less time on the most critical tasks. With Phinity and Elasticito, freed from the tyranny of spreadsheets and tedious reports, your business will rise above the risks.
So how do you determine the risk impact of a vendor? If you still have questions, why not arrange a call with Elasticito for your free consultation? Our team will be happy to assist you on your vendor risk management journey.
Also see our other blog articles on the topic here, here and here.

