Attack Surface Management: How To Enable Your Company’s Cyber Defence
In a new worldwide digital work landscape accelerated by the Covid-19 pandemic, the threats posed by Shadow IT and attack surface expansion have been turbocharged. The attack surface of businesses has rapidly expanded and includes publicly facing infrastructure, domains, users, email addresses, social media, IoT, Cloud and web components. These complex attack surfaces have evolved at an ever-increasing rate, making their management and control difficult. And as its digital attack surface expands, so does the number of potential attacks a business could suffer. Considering that the digital attack surface will only continue to evolve in the future, businesses that are aware of and understand their attack surface will be better enabled to adjust their risk posture to defend themselves.

Shadow IT & Digital Attack Surface
Shadow IT resources include software, apps, systems and devices that are not approved by the organisation’s IT security team. Common examples include Cloud SaaS solutions, productivity apps, messaging apps on corporate-owned devices, physical devices, social media apps, and Cloud storage platforms. Called “Shadow” IT to reflect the exclusion of organisational security teams in the analysis, approval and deployment of these resources, IT security often only become aware of their existence when data breaches have already occurred. In a report published in 2016, Gartner warned that a third of successful breaches experienced by organisations in 2020 would be on their Shadow IT resources. The Ponemon Institute’s Cost of a Data Breach Report noted that in 2020, data breaches, on average, cost companies $3.86 million. This is a stark reminder that not only is prevention of such attacks important, but also ensuring effective visibility and detection capabilities across the entirety of the organisation are implemented and maintained.
In a symbiotic relationship with Shadow IT, the digital attack surface has also continued to evolve, caused by an increasing number of companies and businesses migrating to cloud based services and platforms. Consisting of known, unknown and rogue assets, the attack surface of a company includes its entire publicly visible network assets and software environment and their access points (vectors): domains and subdomains, open databases and ports, SSL certificates, servers, VPN’s, misconfigured services, forgotten environments, exposed assets, third party vendors and IoT devices. As the potentiality of cyber-attacks increases in relation to the growth of an attack surface, being aware of the attack surface as well as keeping it as small as possible is an imperative security task.

By gaining access to a Shadow IT resource or a business’s infrastructure via an attack vector, cyber-attackers are able to penetrate networks and file systems, create persistent user accounts as administrators, open network ports, change digital certificates and access registries, perform website injections, enter or extract data, attack supply chains, target users via waterholes or spear phishing, exploit third parties, deliver mobile malware, go after social media and set up lookalike infrastructure. Many of these attack vectors and Shadow IT resources are difficult to maintain visibility of, or they become lost, forgotten, inaccessible and invisible as time passes and new systems are implemented.
Driving this exposure is the massive shift to remote work, with users inadvertently adapting, innovating and collaborating to remain productive. Highlighting the impact virtual and remote workspaces have had in 2020, the Cost of a Data Breach Report noted that 70% of respondents believed remote work was only expected to increase the cost of a potential data breach. As a result of rapid digital transformation in the modern world, new attack vectors are constantly created against which traditional IT security solutions are simply ineffective. To mitigate these risks, organisations should implement effective attack surface management protocols, procedures and tools.
Managing the Attack Surface
Attack surface management (ASM) is the continuous process of discovering, identification, classification, prioritisation and monitoring of an entity’s digital footprint. ASM can make use of Open Source Intelligence (OSINT) to collect information relevant to the organisation. This information is analysed and classified, whereafter it’s prioritised based on category and sensitivity. As monitoring and analysis are ongoing in ASM, organisations are able to identify and address weakness and vulnerabilities as they arise. In doing so, businesses can actively reduce their attack surface while also improving their cyber security posture. ASM also enables organisations to strengthen customer relationships and business partnerships whilst simultaneously realising increased transparency.
The Importance of ASM
It is the goal of cybersecurity professionals to identify all of the attack surfaces and reduce their size, thereby reducing the risk of attack; removing redundant assets, applications and services, reducing entry points available to untrusted users, conducting regular network and OSINT scans, obfuscating header information, maintaining certificates and encryption levels and regular patching are all methods employed to reduce the attack surface. However, while implementing the above measures are effective, it does not prevent the failure of security controls.
As illustrated in Figure 1 below, effective ASM tools enable companies to identify and monitor the risk surface of their 1) application weaknesses, 2) SSL/TLS vulnerabilities and 3) possible vulnerabilities/patches. By taking steps to effectively reduce these identified risks, the attack surface of the organisation is reduced and constant visibility of assets maintained.
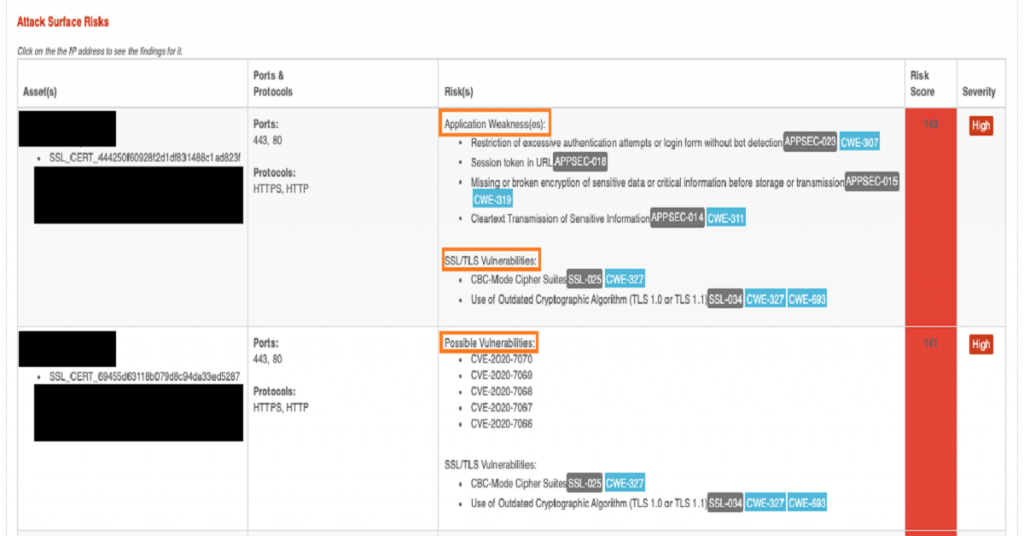
Figure 1: ASM identification and monitoring illustration
The true enormity of an organisation’s attack surface can only be understood by investing in effective ASM tools that provide real time attack surface analysis and vulnerability management.
For more information, contact the Elasticito Team.
