Ransomware: How Susceptible Is Your Organisation? – Part 1

Ransomware has become a critical cyber security threat, causing significant disruption and financial losses to organisations worldwide. This malicious software encrypts valuable data, holding it hostage until a ransom is paid, often leaving businesses in a precarious position. The rise in Ransomware attacks has led to a growing need for robust defence strategies and increased awareness among organisations of all sizes and sectors. To tackle this evolving threat, organisations must understand their vulnerabilities and implement comprehensive protection measures as the weakest and most vulnerable will be targeted. This article explores the business impact of Ransomware, identifies high-value targets within organisations, and examines common attack vectors in the financial sector. It also delves into defence-in-depth strategies, the use of threat intelligence for prevention, crisis management, and the importance of cyber security governance. By addressing these key areas, organisations can enhance their Ransomware resilience and better protect their critical assets.
The Business Impact of Ransomware
Ransomware attacks have become a significant threat to organisations, causing substantial financial losses, operational disruptions and data exposure. The impact of these attacks extends far beyond the ransom demand itself, affecting various aspects of a business’s operations and reputation.
Operational Disruption
One of the most immediate and severe consequences of a Ransomware attack is the disruption to business operations and data exposure leading to regulatory fines. When systems are compromised, organisations often face prolonged periods of downtime, which can have a devastating effect on productivity and revenue. According to a study, 61% of businesses hit by Ransomware experienced an average of 21 days of downtime in 2021. This downtime can paralyse an organisation’s ability to service clients, sell or produce products, and carry out essential functions.
The impact of operational disruption can be felt across various sectors. For instance, in December 2022, the André Mignot hospital in Paris had to shut down its phone and computer systems due to a Ransomware attack, putting patients’ lives at risk. Similarly, manufacturing sites may be unable to operate, online services may become inaccessible to customers, and finance departments may be unable to pay staff and suppliers.
Reputational Damage
A successful Ransomware attack can severely damage an organisation’s reputation, leading to long-term consequences. Customers, employees, investors, and other stakeholders may view the attack as an indication of weak security practises, potentially leading to a loss of trust and business opportunities .
A survey conducted by Field Effect revealed that almost 40% of respondents ranked reputation damage as their top concern following a data breach . This concern is well-founded, as 77% of Ransomware attacks in 2021 included a threat of data leaks. The exposure of sensitive information, such as customer data or trade secrets, can further exacerbate reputational damage and lead to legal repercussions.
Long-Term Financial Consequences
The financial impact of a Ransomware attack extends far beyond the initial ransom demand. Organisations must consider various costs associated with the attack and its aftermath:
- Remediation costs: According to a survey by Sophos, average remediation costs increased from $761,106 in 2020 to $1.85 million in 2021. These costs include business downtime, lost orders, and operational expenses.
- Legal and regulatory consequences: Organisations may face substantial fines and legal costs, especially if personal data is compromised. For example, T-Mobile faced a $350 million settlement following a massive data breach in 2021.
- Cyber security investments: To prevent future attacks, organisations often need to invest in improved security measures, including hardware, software, and specialist support.
- Insurance implications: A Ransomware incident can adversely affect an organisation’s cyber insurance renewal, potentially leading to increased premiums or difficulty in securing suitable coverage.
- Long-term business impact: In some cases, the financial strain of a Ransomware attack can threaten the very existence of an organisation, particularly for smaller businesses.
The cumulative effect of these financial consequences can be substantial. For instance, FedEx experienced an estimated loss of $300 million due to the Petya cyber attack in 2017.
In conclusion, the business impact of Ransomware is multifaceted and far-reaching. Organisations must recognise the potential for operational disruption, reputational damage, and long-term financial consequences when assessing their cyber security strategies and incident response plans.
Identifying High-Value Targets Within Your Organisation
To effectively protect an organisation from Ransomware attacks, it is crucial to identify and safeguard high-value targets. These targets, often referred to as “crown jewels,” represent the most critical information assets that could cause major business impact if compromised. In fact, information assets can represent more than 80% of an organisation’s total value.
Data Classification
Data classification is a cornerstone of modern information management and plays a vital role in identifying high-value targets. This process involves systematically organising and labelling data according to its level of sensitivity, value, and importance to an organisation. By categorising data, businesses can prioritise their protection efforts and allocate resources based on the criticality of information.
Typically, data is classified into categories such as public, internal, confidential, and highly confidential, depending on the level of security required. This classification enables organisations to apply different levels of security based on the nature of the data, such as personally identifiable information (PII), protected health information (PHI), or financial data.
The data classification process involves several steps:
- Data inventory: Create a comprehensive list of all information assets.
- Define classification criteria: Establish criteria based on data origin, sensitivity, and regulatory requirements.
- Categorise data: Apply the defined criteria to categorise the data.
- Implement security controls: Apply appropriate security measures based on the classification.
- Regular review: Conduct periodic reviews to maintain the relevance of the classification scheme.
Business Impact Analysis
A Business Impact Analysis (BIA) is an essential tool for identifying high-value targets and assessing the potential consequences of a Ransomware attack. The BIA helps organisations to:
- Identify specific controls and cross-reference them with the CIS Controls Self Assessment Tool (CIS CSAT) assessment.
- Determine unique organisational assets and estimate the costs of a successful Ransomware attack against those assets.
- Build a 12-month risk profile for each defined asset using the CIS Controls v7.1 and v8.
By conducting a BIA, organisations can drill down into the risk to their digital assets and determine the most effective ways to reduce Ransomware risk across multiple assets. This analysis enables businesses to clearly communicate cyber risk profiles and potential mitigation techniques to both technical and non-technical stakeholders, fostering consensus and support for cyber security initiatives.
Crown Jewel Protection
Protecting an organisation’s “crown jewels” requires a sophisticated approach to counter highly motivated and well-funded adversarial threats. The Information Security Forum (ISF) has developed a structured and systematic five-phase process called the ISF Protection Process to deliver comprehensive, balanced, and end-to-end protection for these critical assets.
This process helps organisations to:
- Identify mission-critical information assets
- Assess the adversarial threats to these assets
- Determine the most appropriate methods of protection
- Implement approaches that ensure comprehensive and balanced protection
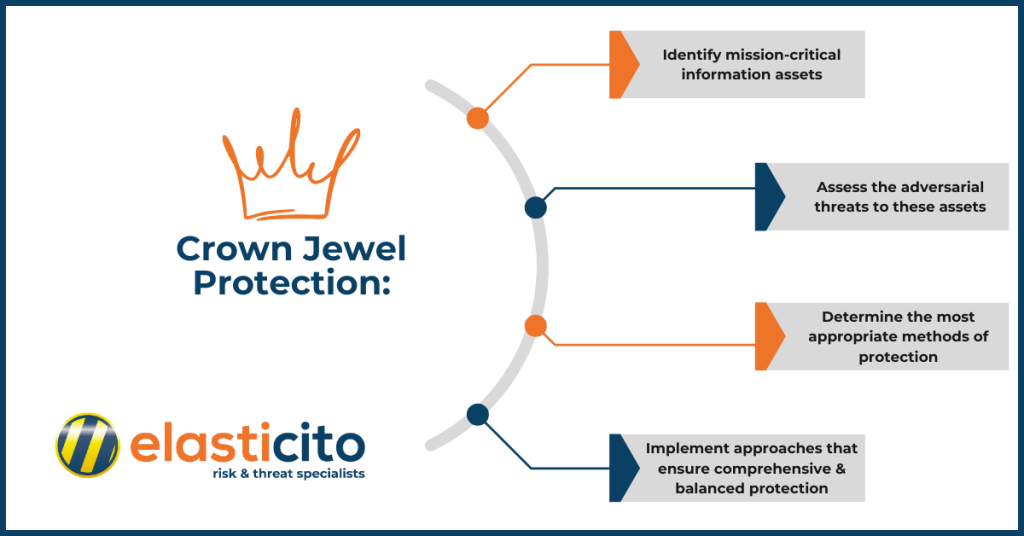
By focusing on crown jewel protection, organisations can allocate resources more effectively and implement tailored security measures to safeguard their most valuable assets from Ransomware attacks.
Ransomware Attack Vectors in the Financial Sector
The financial sector has become a prime target for Ransomware attacks due to the valuable customer information and financial data it possesses. These attacks have seen a significant increase in recent years, with a 520% rise observed between March and June 2020 compared to the same period in 2019. This trend has continued, with a 151% increase in Ransomware attacks reported in the first six months of 2021 compared to the same period in 2020.
Supply Chain Attacks
Supply chain attacks have emerged as a critical concern for financial institutions. These attacks occur when cybercriminals breach an organisation through a compromised third-party vendor in their supply chain. The European Union Cyber security Agency (ENISA) predicts a fourfold increase in supply chain attacks in 2021 compared to 2020.
Key points to consider:
- 66% of compromised suppliers either did not know or failed to report that they were breached.
- Advanced Persistent Threats (APTs) account for 50% of observed supply chain attacks.
- The Kaseya attack in 2021 demonstrated how threat actors could exploit software vulnerabilities to spread Ransomware through managed service providers (MSPs) to their customers.
To mitigate supply chain risks, financial institutions should implement a Zero Trust Architecture with secure Privileged Access Management policies.
Insider Threats
Insider threats pose a significant risk to financial services organisations, as malicious individuals within the organisation can bypass security measures more easily due to their knowledge of internal protocols and systems. The 2020 Ponemon Institute Cost of Insider Threats Report found that the frequency of insider threats has risen by 47% over the last two years, with costs increasing by 31% since 2018.
Key statistics:
- 30% of all breaches were caused by insider threats in 2020.
- 59% of employees who leave their employment take confidential business information with them.
- 65% of respondents admitted to taking proprietary and confidential data that could affect their former company’s business competitiveness.
Financial institutions should implement robust monitoring systems and digital forensics to detect potential insider threats and analyse suspicious user behaviour.
Cryptocurrency-Related Risks
The rise of cryptocurrencies has introduced new risks to the financial sector. Crypto-assets lack intrinsic economic value and are often used as instruments of speculation, making them highly volatile and risky. Their use in financing illicit activities, including Ransomware attacks, has raised concerns about money laundering, market integrity, and consumer protection.
Key risks associated with cryptocurrencies:
- Consumer protection risks, including misleading information and the absence of complaint procedures or recourse mechanisms.
- Potential for market manipulation due to lack of price transparency and low liquidity.
- Financial stability implications through wealth effects, confidence effects, financial sector exposures, and their use as a form of payment.
To address these risks, financial institutions should implement robust cyber security measures, enhance their threat intelligence capabilities, and develop comprehensive incident response plans. By focusing on these key attack vectors and implementing appropriate safeguards, financial organisations can better protect themselves against the evolving threat of Ransomware attacks.
Implementing Defence-in-Depth Strategies
Implementing a robust defence-in-depth strategy is crucial for organisations to protect themselves against the evolving threat of Ransomware attacks. This approach involves layering multiple security measures to create a comprehensive defence system that can effectively mitigate risks and prevent unauthorised access to sensitive data.
Perimeter Security
Perimeter security has long been a cornerstone of network defence, but the landscape of cyber threats has evolved significantly. In the early days of the internet, attackers primarily focused on exploiting simple vulnerabilities in perimeter defences, such as weak passwords on login services. However, as organisations improved their perimeter security, attackers shifted their focus to targeting user devices directly, gaining immediate access to files and resources.
Recent changes, such as Microsoft’s modifications to macro defaults, have forced attackers to adapt their strategies once again. They are now increasingly targeting products on the network perimeter, such as file transfer applications, firewalls, and VPNs, by exploiting zero-day vulnerabilities. This shift in tactics highlights the importance of maintaining robust perimeter security measures.
To enhance perimeter security, organisations should:
- Regularly assess and update perimeter defence systems
- Implement strong authentication mechanisms
- Monitor and log all perimeter traffic
- Conduct regular vulnerability assessments and penetration testing
Network Segmentation
Network segmentation is a critical component of a defence-in-depth strategy. It involves dividing a larger network into smaller sub-networks with limited inter-connectivity, effectively controlling traffic flows and restricting attacker lateral movement. This approach prevents unauthorised users from accessing the organisation’s intellectual property and data.
Key benefits of network segmentation include:
- Improved network performance by reducing traffic congestion
- Enhanced security by limiting the spread of malware and cyber attacks
- Easier compliance with regulations such as PCI DSS
- Reduced time and cost in recovering from data breaches
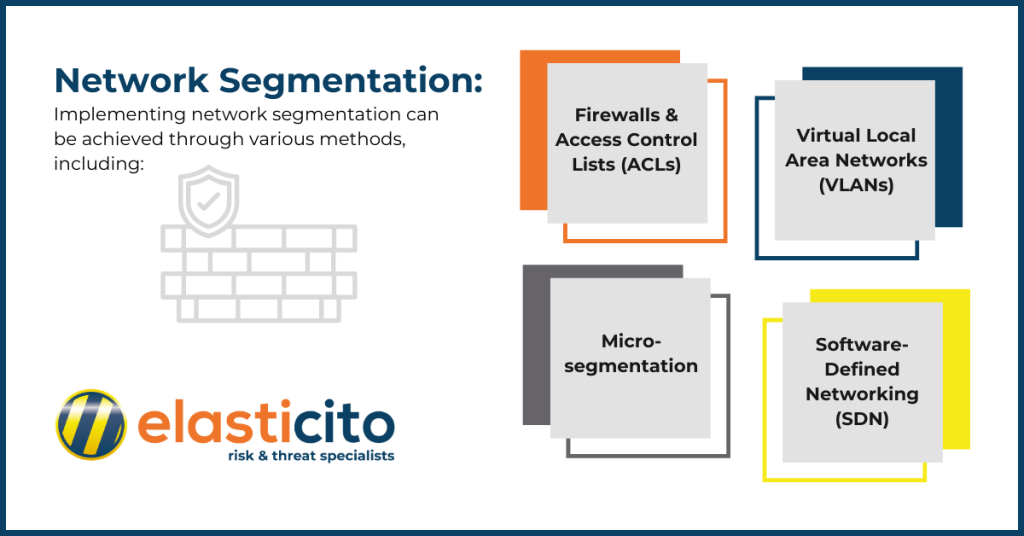
Implementing network segmentation can be achieved through various methods, including:
- Virtual Local Area Networks (VLANs)
- Firewalls and Access Control Lists (ACLs)
- Software-Defined Networking (SDN)
- Micro-segmentation
When implementing network segmentation, organisations should follow the principle of least privilege, ensuring that users and devices have only the minimum access necessary for their tasks.
Data Encryption
Data encryption is a vital component of a comprehensive defence-in-depth strategy. It protects data wherever it resides across the hybrid multicloud environment, rendering it useless to cybercriminals if compromised . Implementing high-standard encryption has been identified as the third most effective cost-mitigating factor in data breach scenarios.
Key aspects of data encryption include:
- Encrypting data at rest and in transit
- Securing encryption keys
- Implementing application whitelisting
- Enforcing fine-grained access control with consistent policy enforcement
By implementing these defence-in-depth strategies, organisations can significantly enhance their resilience against Ransomware attacks and other cyber threats. It is essential to regularly review and update these measures to stay ahead of evolving attack vectors and maintain a strong security posture.
To Be Continued in Part 2…
Elasticito offers comprehensive cyber security solutions to help protect your organisation from Ransomware attacks. Contact the team for more information.
