Regularly Validating Security Controls with Breach and Attack Simulation
Validating Security Controls is of vital importance for all organisations and is mandated by Cyber Security Frameworks like National Institute of Standards and Technology (N.I.S.T.) who offer a simple high-level way to do this using 5 steps:
- IDENTIFY (CROWN JEWELS)
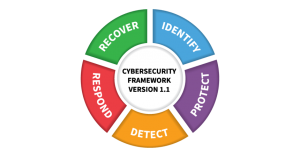
- PROTECT
- DETECT
- RESPOND
- RECOVER
To emphasise the importance of validating Security Control on a regular basis think of pilots doing a pre-flight check and inspection of their aircraft. Not performing these checks and inspections could lead to a loss of license for the pilots and the airline as it is mandatory and so should validating your organisation’s Security Controls.
Simplistically you start by Identifying a Crown Jewel which could be an Endpoint, A Domain Controller or a Business Application. The next step is to detail and understand the attack vectors, which could be infiltration via email or a phishing attack that leads to the download of malicious code via the web gateway over https.
The Protection that would need testing relating to the Endpoint in this example would be the email and web content gateway, possibly the IPS/IDS and Firewall along with the Host Based Endpoint Protection. This is all possible to do with minimal effort using Breach and Attack Simulation and mapping the results to the MITRE ATT&CK Framework to identify gaps and progress.
Just as importantly for each Protection test there should be a corresponding event generated in the SIEM solution which the SOC needs to Respond to, similar to Pilots responding to alerts generated by their instrumentation during flight. Rigorous training, practice and pre-planned response to events leads to rapid mitigation rather than confusion.
All of the above needs repeating on a regular basis with consistancy to ensure that change due to organisational drift hasn’t enabled gaps in your Security Controls specifically relating to their ability to provide Protection, Detection and Response.
If you are interested in seeing how your own organisation’s existing security controls are able to stand up to over 11,000 breach methods, without any damage or impact to your network, contact us to arrange a demonstration.
