Risk Assessment vs. Risk Analysis: An Overview
The recent growth of the extended enterprise has reached a tipping point. That means more organisations are expanding their businesses into the Cloud, staying leaner, and taking advantage of third-party support. At the same time, data breaches are at an all-time high. According to the Ponemon Institute, the average cost of a data breach in 2020 was $3.86 million. Across the globe, there is a growing awareness that organisations need to proactively manage their cyber risk.
Often used as synonyms and easily confused, risk assessment and risk analysis are two unique cyber security processes that IT leaders need to understand to effectively address security issues to prevent data breaches. Below, find out about the differences between these processes and how they fit into a successful cyber security programme.

What is a risk assessment?
A cyber security risk assessment is the process of identifying, analysing and evaluating internal and external risk. In essence, a risk assessment evaluates if the cyber security controls currently implemented by an organisation are adequate relative to the risks and threats it faces. The consequences of unmitigated risks are also covered.
Resources are often wasted or misspent if an organisation chooses not to use a risk assessment to inform their cyber security decisions. Defending against threats that are unlikely to occur also has no value. Similarly, overlooking risks that could cause damage can also be avoided with the valuable information an effective risk assessment provides. Risk assessments are deemed so crucial that many laws and best-practice frameworks such as GDPR (General Data Protection Regulation) and DPA (Data Protection Act) require them to be conducted.
The goal of a risk assessment will depend on the specific organisation and its industry, as well as its compliance regulations. Common goals include developing a risk profile, assessing IT and data assets, or supporting the costs of security countermeasures. In addition to addressing the risks inherent in the company’s current approach to information security, a risk assessment should also consider new risks that may have been created by new technologies or previously undiscovered critical information assets.
A risk assessment framework (RAF) is useful when conducting a risk assessment. A RAF prioritises and outlines information gleaned during an assessment. The RAF should include language understandable to technical and non-technical stakeholders.
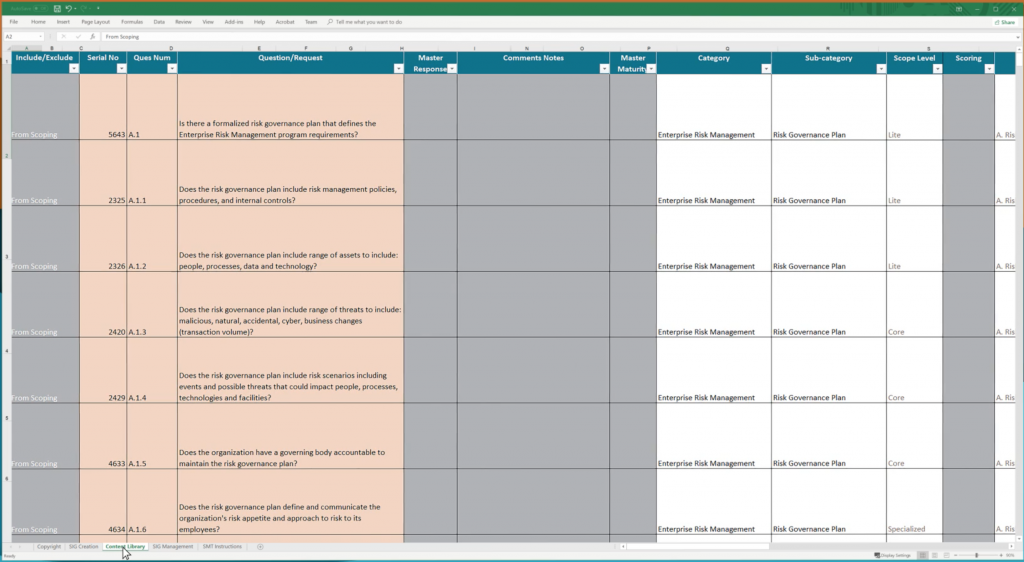
Figure 1: A risk assessment example
What is risk analysis?
A cyber security risk analysis involves identifying the most probable threats to an organisation and analysing the related vulnerabilities of the organisation to these threats. Risk analysis takes your risk assessment efforts to the next level. When analysing risk, you start by focusing on the risk that you identified and then determining the extent of damage it can cause. Risk analysis influences organisational decision making, as it is used to determine the cost of potential threats.
Analysing risk involves either a qualitative or quantitative approach. Qualitative risk analyses aims to predict the likelihood of a risk occurring against its potential effects, ranked low, medium or high. The probability that a risk will occur can also be expressed the same way or categorized as the likelihood it will occur, ranging from 1 – 5 or 0% to 100%. Qualitative risk analyses produces subjective results as the data gathered from respondents is based on their perceptions of the likelihood of a risk occurring and its consequences. Respondents inflate or deflate answers depending on their mental model of risk, and therefor qualitative risk analyses are inconsistent.
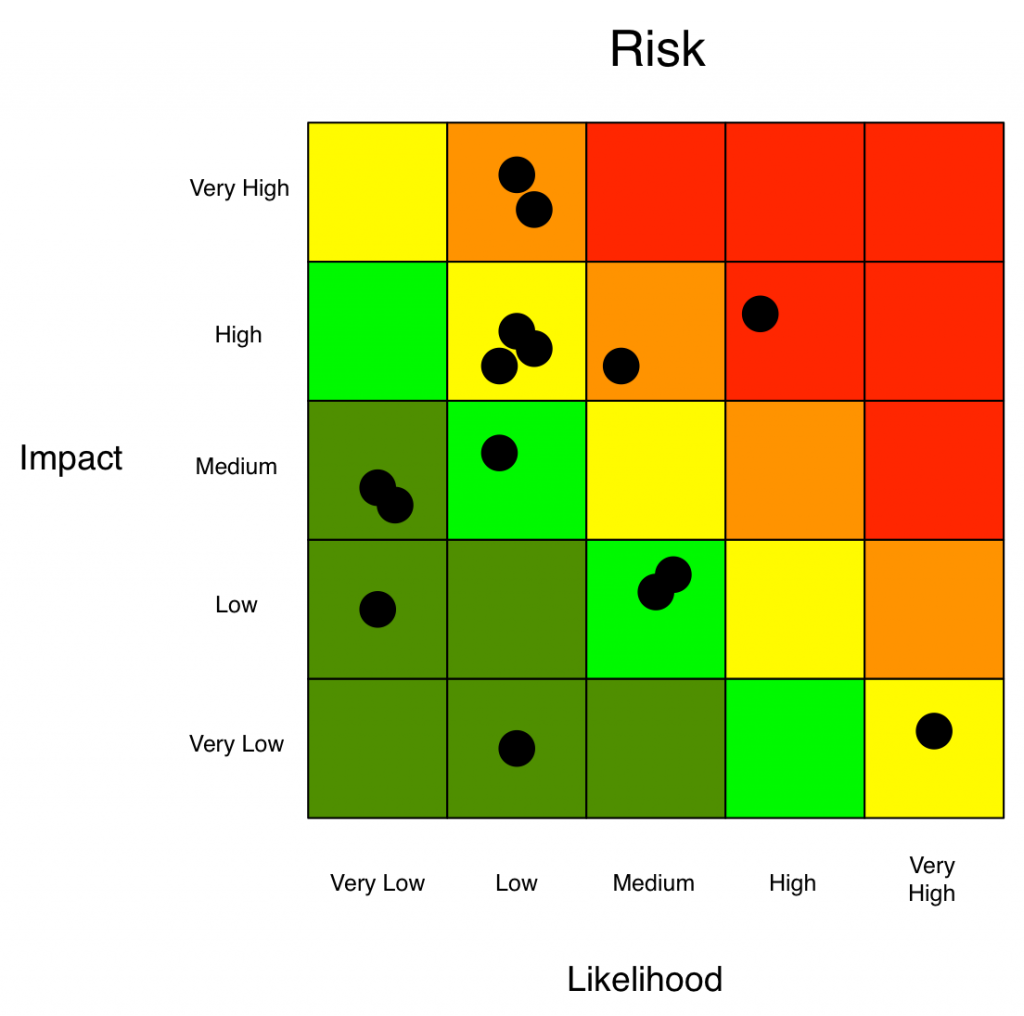
Figure 2: Qualitative Risk Analysis (Source: FAIR Institute)
A quantitative risk analyses estimates the financial impact of each risk. For example if the anticipated cost of a data breach is $3 million and the likelihood of the breach occurring during the current year is 10%, the potential cost of the risk would be $300 000 for the current year. Asset value, threat frequency, safeguard effectiveness, uncertainty and probability are quantified. Quantitative risk analyses yields more objective results as each risk and its consequences is numerically analyzed. Coupled with a risk evaluation model, qualitative risk analyses reduce inconsistencies and tendencies towards bias.
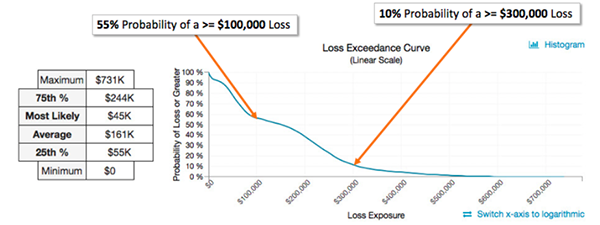
Figure 3: Quantitative Risk Analysis (Source: FAIR Institute)
According to Jack Jones, the purpose of a risk analysis is: “to provide a decision-maker with the best possible information about loss exposure and their options for dealing with it.”
How do risk assessment and risk analysis relate?
Although easily confused, risk assessment and risk analysis are distinct processes with different functions within organisations. However, the best results are achieved when these processes inform each other. The information gathered during a risk assessment is investigated during a risk analysis; this enables the development and enactment of an effective risk management plan for an organisation. Finally, risk is continually monitored and strategies updated accordingly.
While large data breaches often make the news headlines, small and medium businesses are also at risk because they tend to neglect cyber risk management and prevention. Your cyber risk management plan is vulnerable to failure should you be neglecting the following points:
- Identifying and patching vulnerabilities. Your defense strategies have vulnerabilities. Without examining and identifying these weak points, your cyber management strategies are destined to fail.
- Detection of threats. Once a malicious entity has infiltrated your system, they have to be contained and eliminated as soon as possible. Early detection and alert systems are vitally important to limit potential damage.
- Education and creating a culture of awareness. All employees should be informed regarding cyber risks and threats. Best practices should be communicated with all staff member.
- Response and communication. Develop a plan of action in the event of a data breach or malicious intrusion. Once the threat has been eliminated, the team needs to inform the organisation, stakeholders and third parties of any downtime or impacts.
In a new worldwide digital work landscape accelerated by the Covid-19 pandemic, the threats posed by Shadow IT and attack surface expansion have been turbocharged. Managing an organisation’s cyber security risk has become an increasingly complex task: outsourcing, the use of third party vendors, Cloud migration, mobile technologies and remote access have increased cyber risk exposure. Real-time visibility of these risks is impossible when risk assessments are conducted manually. Automating the risk assessment, analysis and management processes remarkably reduces expenditure on time, cost and human resources.
No longer only a technology issue, cyber risk has evolved into an organisational problem. Elasticito’s solutions and services enable cyber risk professionals to focus on analysis, not admin. Contact us for more information.
