Was the Telecom Namibia Data Breach Predictable and Avoidable? A Supply Chain Risk Management Perspective

Introduction
One Tue 10th, December 2024 a notice was published by a Threat Actor ransomware group called Hunter International stating that Telecom Namibia Limited was allegedly hacked.
The objective of this post is to examine this incident from a Supply Chain Risk Management (SCRM) perspective. To assist prospects and existing customers in setting up and maturing their SCRM programs, I always recommend reviewing past incidents to understand if any of the incidents were predictable and avoidable and what mitigating steps should have been taken by all parties.
Telecom Namibia (TN) is a great case in point and all the evidence surrounding this incident is still fresh. At present the incident is still under investigation to determine the root cause. However, if I was a betting person, I would wager that the evidence below is part if not all of the cause of the breach.
Here’s a brief description of the events leading up to this breach.
Back on 18th October 2024, CVE-2024-37404 relating to a product called Ivanti Connect Secure was published on the NIST NVD Database. The description of this vulnerability was:
“Improper Input Validation in the admin portal of Ivanti Connect Secure before 22.7R2.1 and 9.1R18.9, or Ivanti Policy Secure before 22.7R1.1 allows a remote authenticated attacker to achieve remote code execution”
Additionally, on 12th November 2024, CVE-2024-47906 was published along with another 13 other CVE’s relating to Ivanti Connect Secure. This one stating:
“Excessive binary privileges in Ivanti Connect Secure before version 22.7R2.3 (Not Applicable to 9.1Rx) and Ivanti Policy Secure before version 22.7R1.2 (Not Applicable to 9.1Rx) allows a local authenticated attacker to escalate privileges.”
Here’s a complete list and Ivanti Reference articles.
References:
- https://forums.ivanti.com/s/article/Security-Advisory-Ivanti-Connect-Secure-and-Policy-Secure-CVE-2024-37404?language=en_US
- https://nvd.nist.gov/vuln/detail/CVE-2024-39710
- https://nvd.nist.gov/vuln/detail/CVE-2024-39711
- https://nvd.nist.gov/vuln/detail/CVE-2024-39712
- https://nvd.nist.gov/vuln/detail/CVE-2024-11004
- https://nvd.nist.gov/vuln/detail/CVE-2024-38655
- https://securityonline.info/cve-2024-37404-critical-rce-flaw-discovered-in-ivanti-connect-secure-policy-secure-poc-published/
- https://nvd.nist.gov/vuln/detail/CVE-2024-11006
- https://nvd.nist.gov/vuln/detail/CVE-2024-11005
- https://nvd.nist.gov/vuln/detail/CVE-2024-11634
- https://nvd.nist.gov/vuln/detail/CVE-2024-11633
- https://nvd.nist.gov/vuln/detail/CVE-2024-9844
- https://nvd.nist.gov/vuln/detail/CVE-2024-9420
- https://forums.ivanti.com/s/article/December-2024-Security-Advisory-Ivanti-Connect-Secure-ICS-and-Ivanti-Policy-Secure-IPS-Multiple-CVEs?language=en_US
- https://nvd.nist.gov/vuln/detail/CVE-2024-11007
- https://nvd.nist.gov/vuln/detail/CVE-2024-37377
- https://nvd.nist.gov/vuln/detail/CVE-2024-47907
- https://nvd.nist.gov/vuln/detail/CVE-2024-47906
- https://nvd.nist.gov/vuln/detail/CVE-2024-37401
- https://forums.ivanti.com/s/article/Security-Advisory-Ivanti-Connect-Secure-ICS-Ivanti-Policy-Secure-IPS-Ivanti-Secure-Access-Client-ISAC-Multiple-CVEs?language=en_US
- https://nvd.nist.gov/vuln/detail/CVE-2024-39709
- https://nvd.nist.gov/vuln/detail/CVE-2024-38656
- https://nvd.nist.gov/vuln/detail/CVE-2024-37400
Reference CVEs:
- CVE-2024-11007 [High] : Command Injection Vulnerability, RCE Vulnerability [CVSS: 7.2, EPSS: 0.05%]
- CVE-2024-37400 [High] : Out-of-Bounds Read Vulnerability [CVSS: 7.5, EPSS: 0.04%]
- CVE-2024-38656 [Critical] : Argument Injection Vulnerability, RCE Vulnerability [CVSS: 9.1, EPSS: 0.04%]
- CVE-2024-39709 [High] : Privilege Escalation Vulnerability [CVSS: 7.8, EPSS: 0.04%]
- CVE-2024-11004 [Medium] : Reflected XSS Vulnerability [CVSS: 6.1, EPSS: 0.04%]
- CVE-2024-39710 [Critical] : Argument Injection Vulnerability, RCE Vulnerability [CVSS: 9.1, EPSS: 0.04%]
- CVE-2024-11005 [Critical] : Command Injection Vulnerability, RCE Vulnerability [CVSS: 9.1, EPSS: 0.04%]
- CVE-2024-47906 [High] : Use-after Free Vulnerability, RCE Vulnerability [CVSS: 7.8, EPSS: 0.04%]
- CVE-2024-11633 [Critical] : Argument Injection Vulnerability, RCE Vulnerability [CVSS: 9.1, EPSS: 0.04%]
- CVE-2024-9420 [High] : Use-after Free Vulnerability, RCE Vulnerability [CVSS: 8.8, EPSS: 0.04%]
- CVE-2024-37401 [High] : Out-of-Bounds Read Vulnerability [CVSS: 7.5, EPSS: 0.04%]
- CVE-2024-47907 [High] : Stack-based Buffer Overflow [CVSS: 7.5, EPSS: 0.05%]
- CVE-2024-37377 [High] : Heap-based Buffer Overflow Vulnerability [CVSS: 7.5, EPSS: 0.04%]
- CVE-2024-9844 [High] : Client-Side Enforcement of Server-Side Security [CVSS: 7.1, EPSS: 0.04%]
- CVE-2024-11634 [Critical] : Command Injection Vulnerability, RCE Vulnerability [CVSS: 9.1, EPSS: 0.04%]
- CVE-2024-39711 [Critical] : Argument Injection Vulnerability, RCE Vulnerability [CVSS: 9.1, EPSS: 0.04%]
- CVE-2024-39712 [Critical] : Argument Injection Vulnerability, RCE Vulnerability [CVSS: 9.1, EPSS: 0.04%]
- CVE-2024-37404 [Critical] : Remote Code Execution Vulnerability [CVSS: 9.1, EPSS: 0.27%]
- CVE-2024-38655 [Critical] : Argument Injection Vulnerability, RCE Vulnerability [CVSS: 9.1, EPSS: 0.04%]
- CVE-2024-11006 [Critical] : Command Injection Vulnerability, RCE Vulnerability [CVSS: 9.1, EPSS: 0.04%]
Date: October 09, 2024 [Updated: December 13, 2024]
Table: 1.1 Reference Black Kite Cyber Risk Ratings Focus Tag for Ivanti Connect Secure
The above list of CVE’s are a Threat Actor’s dream, mainly because organisations that make use of solutions like Ivanti Secure Connect, don’t become aware of these vulnerabilities until it’s tool late. The reason for this is that products like Ivanti Secure Connect are in a blind spot, whereby if an organisation is making use of a Vulnerability Management (VM) solution, then it may not be configured to cover these products (IP range), the VM solution may not be able to detect the vulnerability, and a scan may need to be run for this vulnerability to be highlighted, which may only be done monthly.
Threat Actors don’t have the same blinds spot and time is of the essence to exploit a vulnerability and to at least gain a foothold inside and organisation to enable to the real work to begin, before the vulnerability is patched . While the Threat Actor’s reconnaissance team keep a care watch for these vulnerabilities, step one on who is vulnerable, once discovered, is to do a quick Shodan search for potential victims.
A simple Shodan search on 19th December 2024 for “Pulse Secure” revealed 84 potential targets. Narrowing the search to Nambia, here’s what can be seen in Shodan:
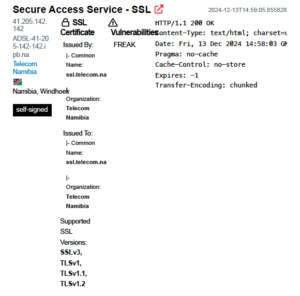
This shows that TN makes use of a solution called Ivanti Connect Secure, which is a secure access VPN that allows remote and mobile users to access corporate resources from any web-enabled device. Drilling down for more detail, this infrastructure was still visible on 13th December 2024:
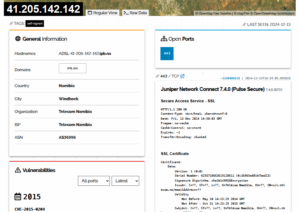
The takeaway points from the above images are:
- Use of Invanti Network Connect 7.4.0 (Pulse Secure)
- Support for SSL3, TLS 1 & 1.1 (no longer recommended for use because they have security issues)
- Certificate that expired on Oct 31, 2019
When classifying a Vendor like Telecom Namibia it should be classified as a Critical Service provider is they are providing essential services and marked for continuous monitoring using a Cyber Risk Ratings Tool to ensure timeous notification of Supply Chain Compromise.
From a Supply Chain Risk Management perspective if an organisation makes use of Black Kite as Cyber Risk Ratings solution, they would have received Invanti Tag alerts relating to Telecom Namibia on 11th October and again on 14th November. They would have also been alerted to the expired certificate and existing support for SSL3, TLS 1 & 1.1 for this TN asset. All of which they could have communicated to the Vendor requesting an explanation and remediation.
Similarly had TN been making use of Black Kite they wouldn’t have had a blind spot; they would have received similar notifications and could possibly have avoided this breach assuming of course that it was the root cause.
Unfortunately, this is not a first for Ivanti: “On April 20, 2021, it was reported that suspected Chinese-state backed hacker groups had breached multiple government agencies, defense companies and financial institutions in both the US and Europe after the hackers created and used a Zero-day exploit for Ivanti Pulse Connect Secure VPN devices.”
Reference: https://en.wikipedia.org/wiki/Ivanti_Pulse_Connect_Secure_data_breach
Conclusion
Looking at the past provides a lesson for the future.
Discover the full range of solutions available at Elasticito.
