The Anatomy of a Data Breach
Arguably no phrase has dominated the tech world the last 24 months more than the term “data breach.” From breaches that have impacted critical infrastructure like the Colonial Pipeline event, to hackers compromising healthcare records at UC San Diego Health. The last two years have been thoroughly saturated by headlines of cyber security mishaps. Yet, despite the prevalence of the breach-centric newscycle, many everyday individuals may not know what exactly a data breach is, how they typically start, and why they occur. Elasticito has dissected the topic and compiled “Anatomy of a Data Breach” to help you understand the ins and outs of the topic.

According to IBM, the average time it takes an organisation to identify that a breach has occurred is a whopping 287 days. IBM furthermore reports that the average time it takes to contain a breach is an astounding 80 days. With 81% of businesses experiencing a cyber attack since the start of the COVID-19 pandemic, it is essential that individuals are familiar with the anatomy of a data breach so that they can keep their data, as well as their colleagues and customers’ data, safe.
With this in mind, here is some helpful background on what data breaches are and why they are so problematic.
What is a data breach?
While it may seem like a complex concept, once the jargon is removed, a data breach is actually really straightforward to explain. According to Trend Micro, a data breach is “an incident where information is stolen or taken from a system without the knowledge or authorisation of the system’s owner.” The purpose of hacking these systems is to use this information for identity theft and fraud purposes.
And while data breaches can be the result of a system or human error, the vast majority of data breaches are the result of cyber attacks, where a cyber criminal gains unlawful access to sensitive system data. This can be done physically by accessing a computer or network to seal local files or by bypassing network security remotely. In fact, 92% of the data breaches in Q1 2022 were the result of cyber attacks.
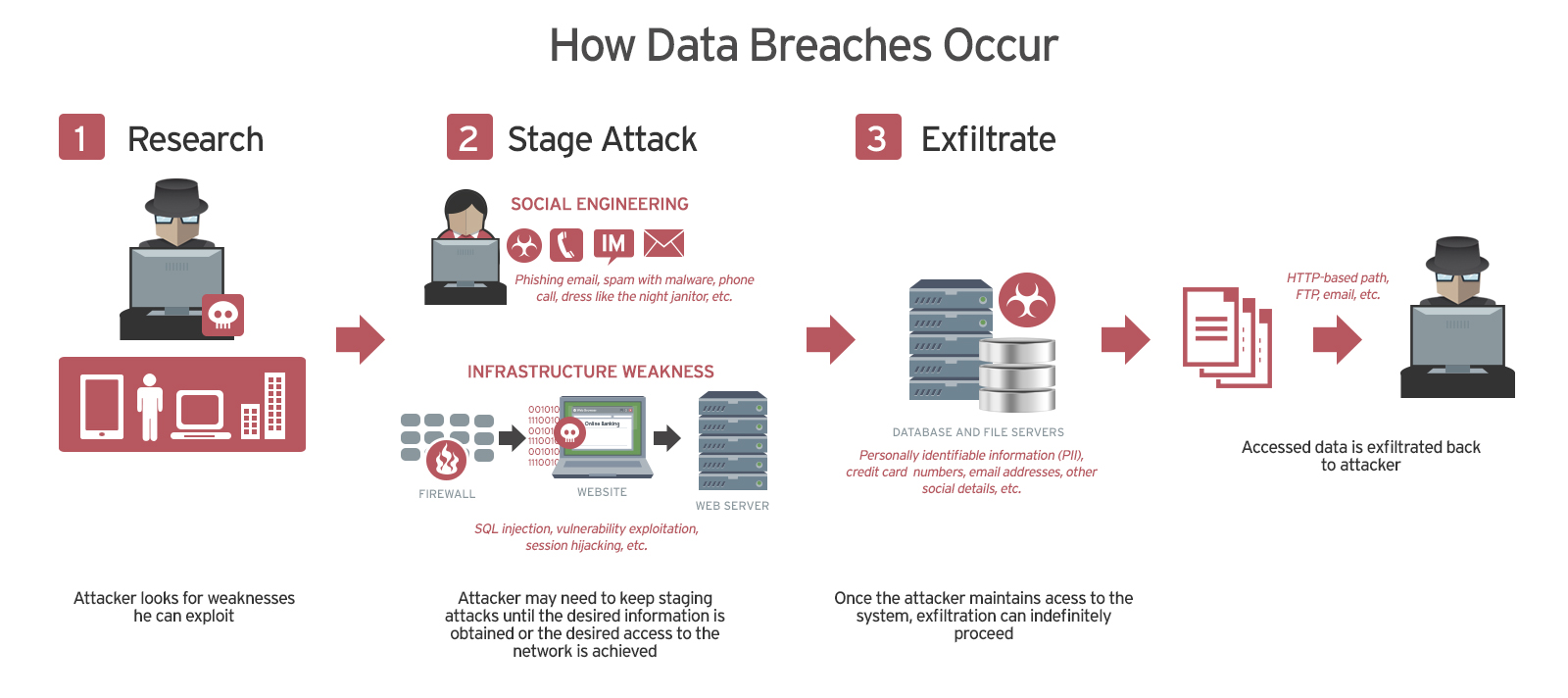
Source: Trend Micro
What kind of data can be breached?
Unfortunately, cyber criminals look to get their hands on any information that they possibly can. This ranges from more obvious sensitive information such as social security numbers and credit card information to more obscure data like past purchase history.
Data breaches can occur in any size organisation, from small businesses to major corporations. They may involve personal health information (PHI), personally identifiable information (PII), trade secrets or other confidential information.
The most common data breach exposures include:
- Personal information, such as credit card numbers, social security numbers, driver’s license numbers and healthcare histories.
- Corporate information, such as customer lists and source codes.
If a data breach results in identity theft or a violation of government or industry compliance mandates, the offending organisation can face fines, litigation, reputation loss and even loss of the right to operate the business.
Are there data breach laws?
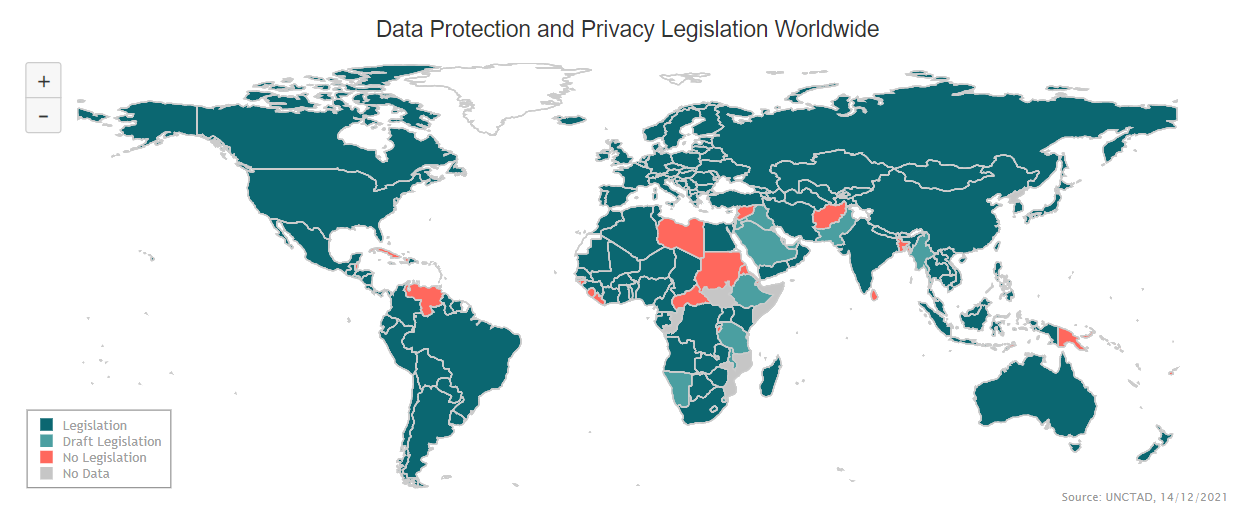
Data breach legislation differs from country to country and region to region. 137 out of 194 countries in the world have put in place legislation to secure the protection of data and privacy. Some countries, however, still do not require organisations to notify authorities in the case of a data breach.
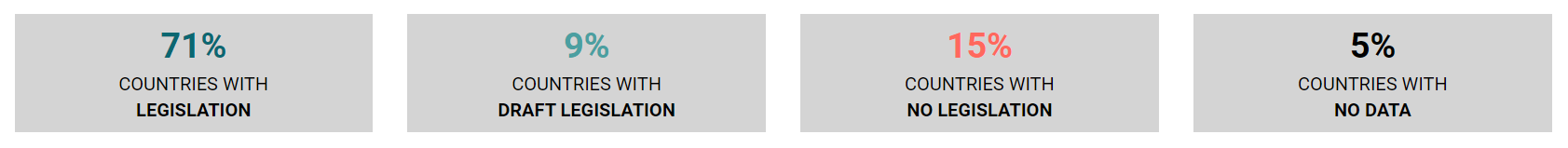
Source: United Nations Conference on Trade and Development
Numerous countries across the world have developed or implemented data privacy and security laws in their countries within the last few years. With the rapid rise in digitisation as a result of the Covid-19 pandemic, the broad implementation of such laws has never been more urgent.
Examples in include Ghana, Kenya, Madagascar, Mauritius, Nigeria, Rwanda, South Africa, Togo, Uganda and Zimbabwe who have been implementing new measures to protect and secure the personal information of their citizens. In countries like the U.S. and Canada, organisations are obliged to notify affected individuals of a data breach under certain conditions.
As of 12 December 2018, under Regulation (EU) 1725/2018 all European institutions and bodies have a duty to report certain types of personal data breaches to the EDPS. Every EU institution must do this within 72 hours of becoming aware of the breach, where feasible. If the breach is likely to pose a high risk of adversely affecting individuals’ rights and freedoms, the EU Institution must also inform the individuals concerned without unnecessary delay.
Companies that suffer a data security breach now also face the challenge of dealing with enforcement agencies, potentially massive fines and possible class action litigation in multiple jurisdictions. Engaging the right advisers can drastically reduce your exposure – both through the decisions you make today and the way you respond to an incident.
What are some of the tactics used to execute data breaches?
Cyber crime is getting more sophisticated each day. However, cyber attack tactics do not have to be cutting-edge or advanced in order to be effective. Here are a few examples of popular tactics used by cyber criminals to execute data breaches:
- Phishing: Phishing is when a cyber criminal pretends to be a legitimate party in hopes of tricking an individual into giving them access to personal information. Phishing is one of the oldest tricks in the book for cyber criminals but it is just as effective as ever. For example, 80% of security incidents and 90% data breaches stem from phishing attempts.
- Malware, ransomware or Structured Query Language (SQL): Malware is malicious software that secretly installs itself on devices – often by way of a user engaging with fake links and content – and quietly gains access to the data on an individual’s device or a business network. Gaining access to systems or applications not only opens the door to malware, but also malware-related activities, such as ransomware and SQL injection.
- Password Attack: Through password attacks, cyber criminals look to gain access to sensitive data and networks by way of “cracking” user passwords and using these credentials to get into networks and extract data from a given network.
- Distributed denial of service (DDoS): Threat actors can use a DDoS attack as a way to distract security administrators so they can gain access to data using alternative methods. Additionally, modifications by the business to mitigate an attack can lead to misconfigurations that create new data theft opportunities.
- Insider threat: Numerous cyber security incidents come from internal users who already have access to or knowledge of networks and systems. This is why monitoring user actions is so critical.
How to spot a possible breach?
Cyber security breaches can be difficult to detect, and the effects can be devastating for businesses of any size. As mentioned above, attackers use a variety of methods to get into systems and steal data, sometimes without anyone even realising what’s happening. This can take months – or even years – to discover, by which point the damage may already be done.
Detecting cyber attacks is a challenge even for the experts, but certain warning signs could indicate that a cyber breach or intrusion is underway. For example:
- Suspicious network activity (e.g. strange file transfers or log-in attempts).
- Sudden changes to critical infrastructure or system passwords and accounts.
- Suspicious files in your system, which may or may not have been encrypted.
- Suspicious banking activities and transactions.
- Inexplicable loss of access to your network, email or social media accounts.
- Leakage of customer details, client lists or company secrets.
- Unusually slow internet connections and intermittent network access.
- Error signs or warnings in browsers, anti-virus or anti-malware tools alerting you to infections.
If you have a business website, you should monitor it for any anomalies that may suggest an attack may be in progress. For example:
- Unexplained inconsistencies or questionable extras in your code.
- Problems with administrative logins or accessing management functions.
- Unexplained changes in traffic volume (e.g. a sudden and drastic drop).
- Unexplained changes in the design, layout or content of your site.
- Performance issues affecting the availability and accessibility of your website.
The best way to stop a data breach is to stop it before it even starts. This includes taking steps from making sure passwords are long and complex to reporting suspicious emails. One of the primary purposes of a network firewall is to detect and mitigate security breaches. By preventing unauthorised access to private networks, firewalls can often prevent breaches from occurring in the first place. However, in cases where security has been compromised, firewalls help alert network administrators so that appropriate action can be taken.
If you do suspect that you have been the victim of a breach, immediately contact your IT department or device provider to notify them and follow subsequent protocols to help them scan, detect, and remediate any issues that exists.
Summary
Data breaches can cause a lot of damage to an organisation, but with proper planning and foresight, the damage can be minimised. To detect breaches properly, you need to have a strong understanding of the systems involved and be proactively on the lookout for signs of trouble. Data breaches are not going away anytime soon so the best defense against them is an offense so make sure to monitor your information and be diligent about your identification information.
While being proactive is a sound strategy for approaching network security, the job can be made easier by utilising analytics software to provide real-time analysis and advanced vulnerability detection. To assist in detection, analytics tools can be used to keep a near-constant eye on system data and possible intrusion attempts. Elasticito can recommend a range of tools to mitigate risk – feel free to contact us here.
