The European financial sector faces increasing cyber threats and operational disruptions. Consequently, the sector is now subject to the Digital Operational Resilience Act (DORA). This article, the second part of our essential guide, follows our initial overview in “Digital Operational Resilience Act: Essential Guide – Part 1”. We now delve into the specific technical cybersecurity requirements and controls mandated by DORA.
Financial entities must implement these systems to strengthen their digital defences, covering critical aspects like encryption, access control, and real-time monitoring. Furthermore, we highlight the importance of contractual clauses with ICT providers and the necessary resource allocation for testing and reporting as institutions navigate DORA compliance in 2025.
DORA Cyber Security Requirements & Technical Controls
DORA’s technical security requirements establish prescriptive standards financial entities must implement across their digital infrastructure ecosystems. These technical specifications transcend generalised guidance by mandating explicit control mechanisms across multiple ICT management domains.
Encryption, Access Control & Network Segmentation
DORA’s cyber security framework fundamentally relies upon sophisticated data protection architectures.
Data Protection: Financial entities must deploy encryption and cryptographic controls predicated upon risk-assessment methodologies to safeguard data availability, authenticity, integrity and confidentiality.
Access Governance: Institutions must formulate explicit policies restricting physical and virtual access to ICT resources, implementing robust authentication protocols aligned with relevant technical standards.
Network Interconnection: DORA explicitly requires infrastructures capable of instantaneous severance when security imperatives dictate. Topologies must demonstrate appropriate segmentation and compartmentalisation to contain propagation risk.
Real-Time Monitoring & Threat Detection Systems
Perpetual vigilance functions as an indispensable Digital Operational Resilience Act compliance requirement. Financial entities must operationalise real-time monitoring capabilities facilitating expeditious identification and remediation of emergent threat vectors.
What specific technical components are required for automated threat detection? Automated threat detection capabilities require implementation of specific technical components, including:
Security Information and Event Management (SIEM) architectural frameworks.
Advanced behavioural analytics incorporating machine learning algorithms.
Prioritised notification systems for incident response teams.
DORA explicitly mandates that organisations maintain evidentiary documentation of ICT-related incidents facilitating subsequent forensic examination. Beyond detection, entities must establish integrated incident management workflows automating classification, handling, and regulatory reporting in accordance with DORA’s stringent notification chronologies.
Overlooking Contractual Clauses with ICT Providers
DORA’s contractual remediation obligations present exceptionally challenging obstacles. Notwithstanding the implementation efficiencies standardised contractual clauses would facilitate, DORA provides no such templates, thereby exponentially increasing remediation complexity.
Essential Contractual Requirements for ICT Providers
Expert Claim: Regulatory accountability remains unequivocally with the financial entity, rendering effective negotiation capabilities instrumental to achieving DORA-compliant contractual arrangements.
Contractual instruments must incorporate:
Unambiguous obligations compelling ICT providers to furnish incident response assistance without supplementary charges or at predetermined cost structures.
Explicit termination provisions including minimum notification periods.
Detailed provisions governing testing regimes, audit entitlements, and exit strategy protocols.
Service Level Agreements (SLAs) consolidated within a singular written document available in a persistent digital or physical format.
Underestimating Resource Needs for Testing & Reporting
Financial institutions systematically underestimate resource requirements necessary for comprehensive DORA implementation. Organisations must execute thorough financial impact assessments encompassing contract review processes, personnel recruitment, and software acquisition.
The Burden of Technical Testing and Documentation
Threat-Led Penetration Testing (TLPT): Executed every three years, this necessitates substantial technical expertise and significant financial resource allocation.
Information Register: Effective January 2025, all financial entities must maintain exhaustive documentation of contractual arrangements with ICT third-party service providers.
Register Preparation: This requires extensive documentation protocols, sophisticated monitoring capabilities, and periodic content refreshment at entity, sub-consolidated, and consolidated levels.
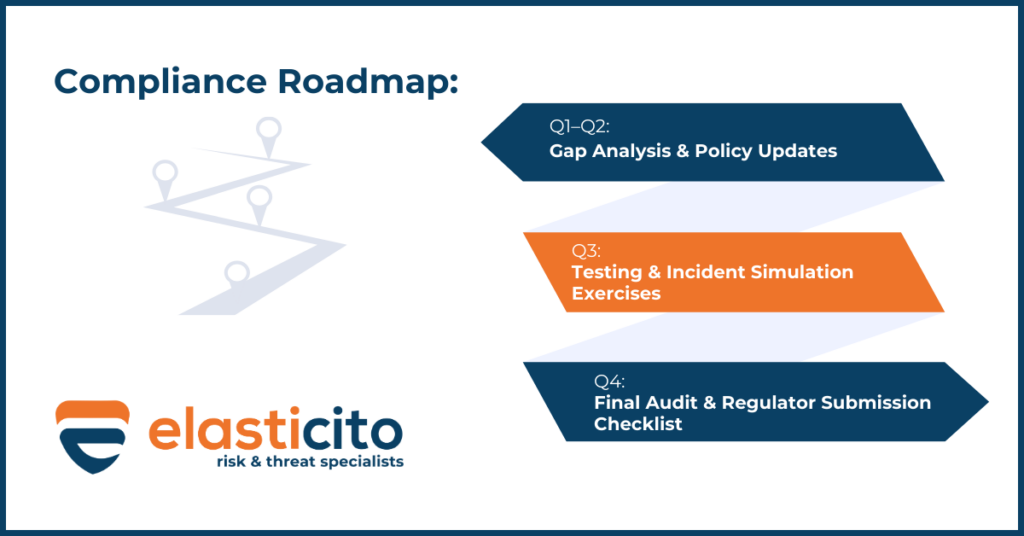
Compliance Roadmap for Financial Institutions in 2025
January 17, 2025 constitutes the definitive DORA enforcement commencement date, necessitating adherence to precisely structured quarterly implementation protocols.
| Period | Priority Focus Area | Key Deliverables |
| Q1–Q2 | Gap Analysis & Policy Updates | Comprehensive gap analysis against five regulatory pillars; submission of Information Registers (RoI) by April 30, 2025. |
| Q3 | Testing & Incident Simulations | Risk-based resilience assessments; scenario-based tabletop exercises; preparation for triennial TLPT. |
| Q4 | Final Audit & Submission | Verification of 4-hour incident notification parameters; finalisation of automated monitoring; internal audit execution. |
Q1–Q2: Gap Analysis & Policy Updates
Early 2025 demands concentrated focus on fundamental assessment activities. Financial entities must execute comprehensive gap analysis protocols evaluating existing ICT risk management frameworks. Concurrently, focus must shift toward preparation of Information Registers (RoI) for submission to National Competent Authorities.
Q3: Testing & Incident Simulation Exercises
Quarter three necessitates prioritisation of operational resilience verification. Emphasis requires placement on scenario-based tabletop exercises simulating significant ICT incidents. Financial entities must also initiate preparations for mandatory Threat Led Penetration Testing (TLPT) for critical ICT components.
Q4: Final Audit & Regulator Submission Checklist
The terminal quarter demands completion of all compliance activities preceding intensified regulatory scrutiny, including the finalisation of automated monitoring systems and internal audit procedures verifying organisational-wide DORA implementation.
Conclusion
In conclusion, the Digital Operational Resilience Act represents a significant paradigm shift in how the European financial sector approaches and manages ICT risk. Part 2 of this guide has illuminated the specific technical security requirements, the critical need for robust contractual clauses, and the structured compliance roadmap for 2025. Successfully navigating these multifaceted requirements demands a proactive and strategic approach to implementation. As the January 17, 2025 enforcement date has now passed, financial institutions must move beyond planning and actively execute their DORA compliance strategies.
Visit Elasticito to take the next crucial step in safeguarding your digital future.
Created: May 9th, 2025
Reviewed: February 11th, 2026






