Ransomware: Facts, Risks, and Countermeasures
Ransomware has been a major threat to cyber security in the past few years. The malware encrypts files, locking them and demanding a ransom to unlock them. These ransomware attacks have affected organisations, hospitals, schools, municipalities and enterprises. Ransomware is becoming more sophisticated and difficult to stop, with attackers increasingly encrypting data before demanding money to decrypt it. One thing is certain: ransomware attacks have many different appearances and come in all shapes and sizes. Continue reading to find out about the latest development in the fight against ransomware.

Malware with a ransom note
Ransomware is a type of malware that is used to encrypt files held on a computer in such a way that they can only be unencrypted by paying a ransom. Victims are told that they must pay the ransom, or risk to lose access to their files forever.
Users are shown instructions for how to pay a fee to get the decryption key. The costs can range from a few hundred dollars to thousands, payable to cybercriminals in currency such as Bitcoin.
How do devices get infected with ransomware?
There are a number of ways ransomware can get into a computer. One of the easiest is through phishing spam. Attachments masquerading as files that users should trust will gain access to a computer, especially if they have built-in social engineering tools that trick users into allowing administrative privileges.
Other than the more aggressive forms of ransomware like NotPetya and malware such as Cryptolocker exploit security holes in order to infect victims.
What are the risks of a malware infection?
There are several things that malware might do once it has invaded your computer. It might encrypt files, download other malware onto the computer, or attempt to gain access to sensitive information, such as passwords and banking details. Currently, the most common action is to encrypt files.
The most important thing to know is that once the files have been encrypted, they cannot be decrypted without a unique digital key that only the attacker has access to. Before the files can be restored, the victim must make a payment to the attacker, who will then send the victim an untraceable message containing a link to an online wallet address where they can send their password in full confidence that it will never be linked back to them.
Some forms of malware might pretend to be a law enforcement agency and tell you that your computer has been involved in illegal activities, such as copyright infringement. They might say that they will release personal information about you unless you pay them a “fine”. However, most malware does not bother with this pretence.
Also in existence is a type of ransomware called leakware or doxware. It tries to extort the victim by threatening to publish sensitive information on their hard drive unless the ransom is paid. Encryption ransomware is the most common type utilised, however.
Ransomware has been around since 1989; that means the cyberattack landscape has expanded and become much more complex. Cloud, wireless, industrial, and Internet of Things (IoT) devices are all connected to one another and constantly sending and receiving data.
Ransomware often infects computers through email and downloads malicious attachments. For example, Locky Ransomware is typically downloaded via phishing emails that attach a malicious Microsoft Word file containing an embedded macro.
The increasing prevalence of ransomware attacks means that businesses need to be prepared: they must be aware of ransomware, have a plan in place for how to respond to an attack, and train employees on what to do if their systems are infected.
Fortunately, employees can take online security training at home just as easily as they can in an office. Some of the best training online is available through the SANS Institute, a trusted source for cyber security certification and research. For organisations that have moved their data to the cloud or use the cloud for backup, it’s also important to use tools such as cloud data encryption to help avoid data breaches.
Join the ransomware revolution
Ransomware was the most common cyber threat to organisations in 2020. An attack on a company creates significant cyber risk to any organisation it does business with. Companies must continuously monitor vendors and trading partners within their supply chains to maintain a real-time assessment of the potential for ransomware attacks.
While Ransomware ranked first among cyber threats in 2020, according to the IBM Security “2021 X-Force Threat Intelligence Index”, it comprised 23 percent of cyberattacks last year.
Black Kite, a leading cyber security ratings provider and Elasticito partner, today introduces the first automated ransomware service that rates companies on their vulnerability to ransomware attacks. The Ransomware Susceptibility Index™ (RSI™) enables companies to gauge the risk of any vendor in minutes.
The RSI inspects, transforms, and models data collected from various open-source intelligence (OSINT) sources and leverages machine learning to approximate ransomware risk. The susceptibility scale ranges from 0.0 (lowest likelihood of attack) to 1.0 (highest likelihood of attack). The patent-pending RSI examines 26 unique controls to calculate index approximations. Black Kite provides all calculation formulas for full transparency.
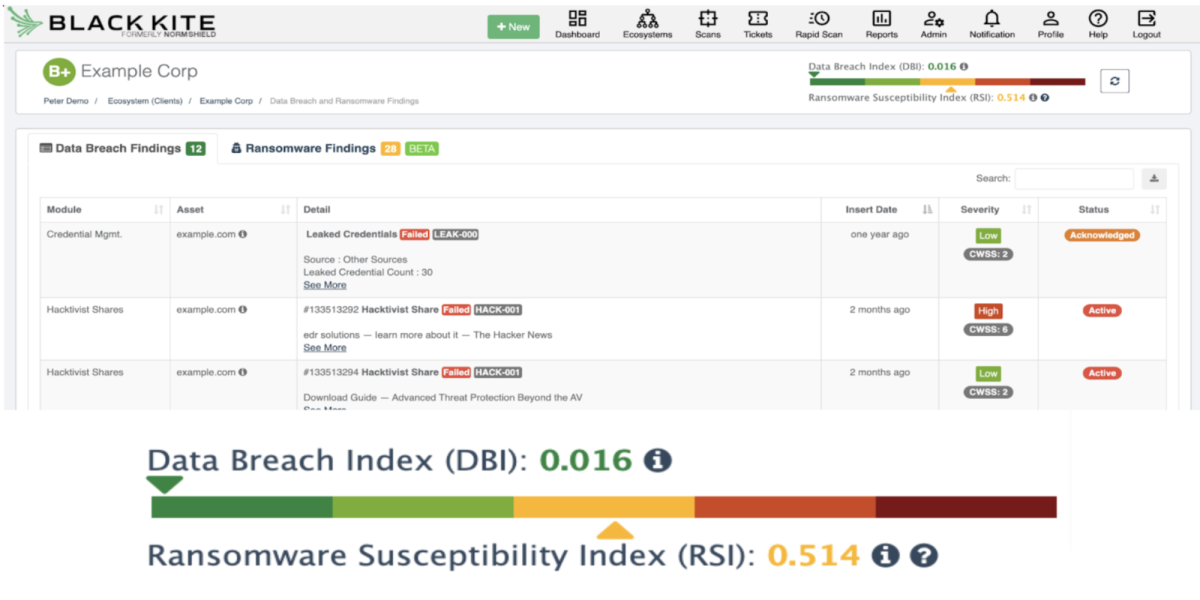
The Ransomware Susceptibility Index shows a score between 0.0 and 1.0. A score of 0.517 means the company has a 51% probability of being hit by ransomware within 12 months.
Conclusion
Ransomware is a type of malware that locks systems and files until victims pay a ransom. It often enters businesses through phishing emails with malicious attachments or links to malicious sites. Ransomware variants almost always opportunistically target victims, infecting an array of devices from computers to smartphones.
Ransomware has indeed become a rapidly evolving threat. Criminals are continually improving their skills to successfully demand ransoms from victims.
If you’re in doubt about the effectivity of Black Kite’s revolutionary RSI development, why not have a 30 minute obligation free call with the team at Elasticito? We’d be happy to assist – contact us here.
