4 Ways to Use Security Ratings Tools to Automate Risk Assessments
Your organisation is at risk of being attacked by cyber criminals. It’s just a fact of life in this digital age. But how great is the risk you’re facing and what can you do to mitigate it? Security ratings tools are an essential part of any good cyber risk management strategy. These tools help organisations understand, control and mitigate all forms of cyber risk. They are so vital, in fact, that they stand as critical components of an effective data protection and risk management strategy. With more and more businesses relying on digital systems for day-to-day operations, the potential for new vulnerabilities also grows — which means greater risks for everyone involved. Here are “4 ways to use security ratings tools to automate risk assessments” which will enable the minimisation of your cyber security risks.

Introduction
The way that third party cyber risk assessments have been conducted in the past has largely been document – and people intensive and has therefore been expensive, manual and slow. As a result, it is rare for companies to regularly assess and monitor anything other than the most critical third parties. As business becomes increasingly digital and companies share data, network access or their facilities, there is a growing need to be able to understand the cyber risk maturity of key vendors and third parties who have access to sensitive data or enterprise systems. It is necessary because it ensures that your key vendors and third parties’ own level of cyber maturity matches your organisation’s expectations.
Below is a snapshot, courtesy of Deloitte, of the various interconnected third-party relationships, often where data and/or network access is granted to the third party:

Source: Deloitte
Companies are not assessing third party cyber risk
A 2021 study by the Ponemon Institute showed that 44% of companies had experienced data breaches as a result of a third party being breached, but yet only 51% of companies surveyed were not regularly assessing and monitoring third party cyber risk.
Traditional risk assessments are cumbersome and inefficient
The traditional method of assessing third party cyber risk is to send a risk assessment questionnaire to a third-party and wait for the external party to review and complete it. Some of the industry standard cyber risk assessment questionnaires can be over 1,500 questions long. It is no wonder that the average response time to complete these questionnaires is currently 4-6 weeks, according to Prevalent.
Here are 4 ways to use security ratings tools to automate risk assessments:
1. Assessing and monitoring critical vendors (micro analysis)
Imagine being able to run a detailed technical cyber risk assessment to conduct micro analysis on evidence based findings and vulnerabilities within 10 minutes of kicking off the risk assessment. That is what is possible with cyber risk rating tools, like Black Kite. Instead of having to wait for weeks for the vendor to respond to your risk assessment questionnaire, technical risk data can be compared with your operational acceptable risk model to rapidly decide whether the particular vendor is an acceptable risk or whether remedial action is required to address areas of concern.
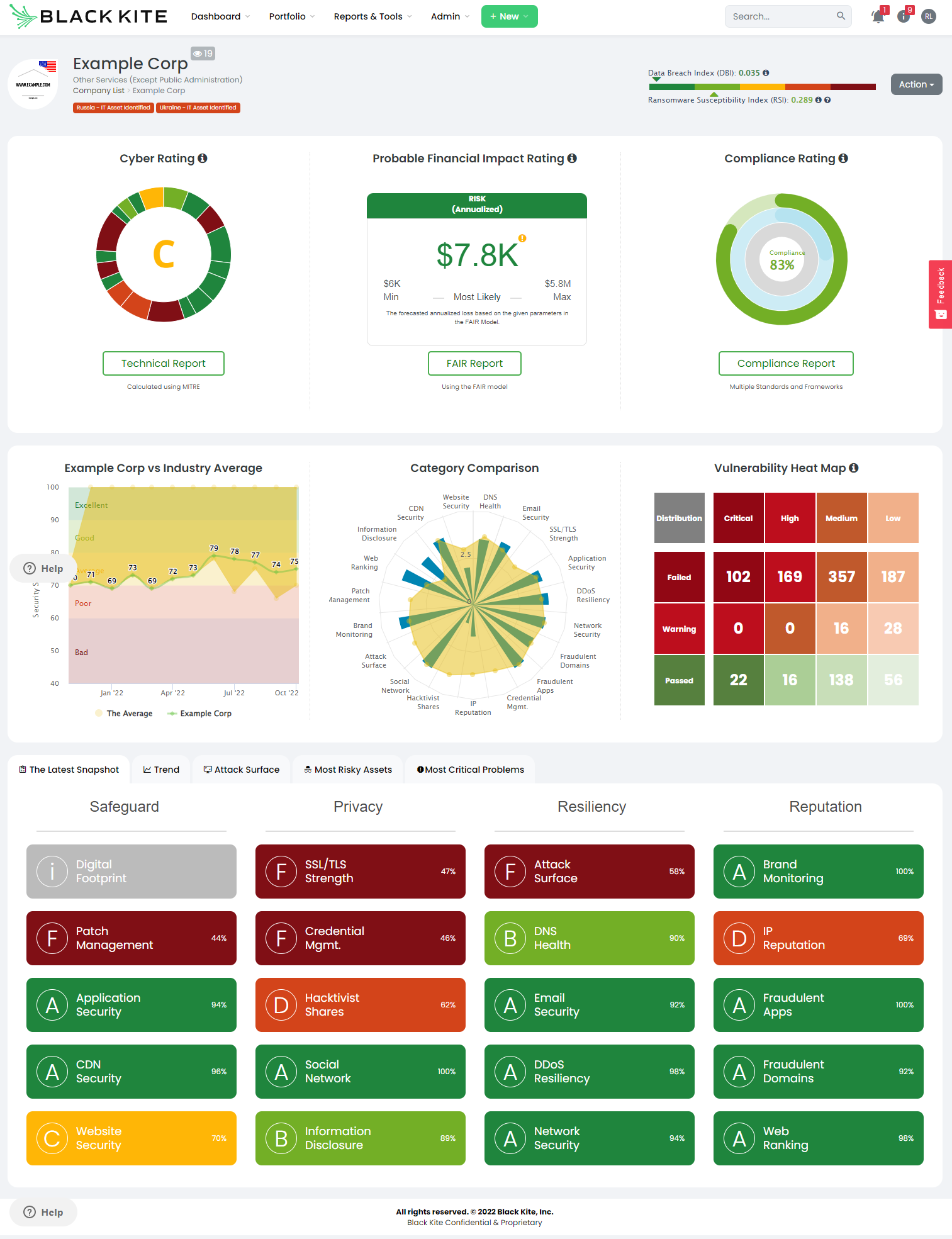
2. Assessing vendor cyber risk for procurement due diligence
Let’s face it, most information security risk professionals are service providers for other internal stakeholder groups. Increasingly, procurement teams are looking to add cyber risk assessments to their vendor short list due diligence checks. If they are having to wait for 4-6 weeks to get a go/no-go opinion on how risky the shortlisted vendors may be from a cyber risk perspective. That is not great service.
Another way to conduct these side-by-side vendor risk comparisons is to consider both technical and probable financial risk. Afterall, if one company is rated B and another B- how can you provide an adequate appraisal of the risk that those companies might pose to your business?
In the Black Kite platform, probable financial impact is calculated using the FAIR model. This presents the financial risk to your company if a third party that has access to your company’s data suffers a breach. Sometimes speaking to the business in the (financial) language that they understand is a more effective way to getting them engaged with cyber risk.

Sometimes however, a side-by-side technical review needs to be conducted. Again, these should be able to be produced in minutes, rather than days or weeks. Here is an example of three HR Management platforms that typically process personal data, compared by cyber risk category:

With this information, the cyber risk, procurement and HR teams can make a rapid, but informed decision about the preferred vendor (from a cyber risk perspective) that they would like to go with.
3. Monitoring vendor risk at scale (macro analysis)
At Elasticito, we are told time and time again by information security and cyber risk teams that they do not have the time, budget or resources to assess and monitor all vendors. That may be true using traditional risk assessment methods, but with security ratings tools, you can assess and monitor tens, hundreds or thousands of third parties economically, rapidly and with ease.
Here is an example dashboard where over 2,000 entities are being monitored, but it is still possible to identify and address risky third parties with ease:
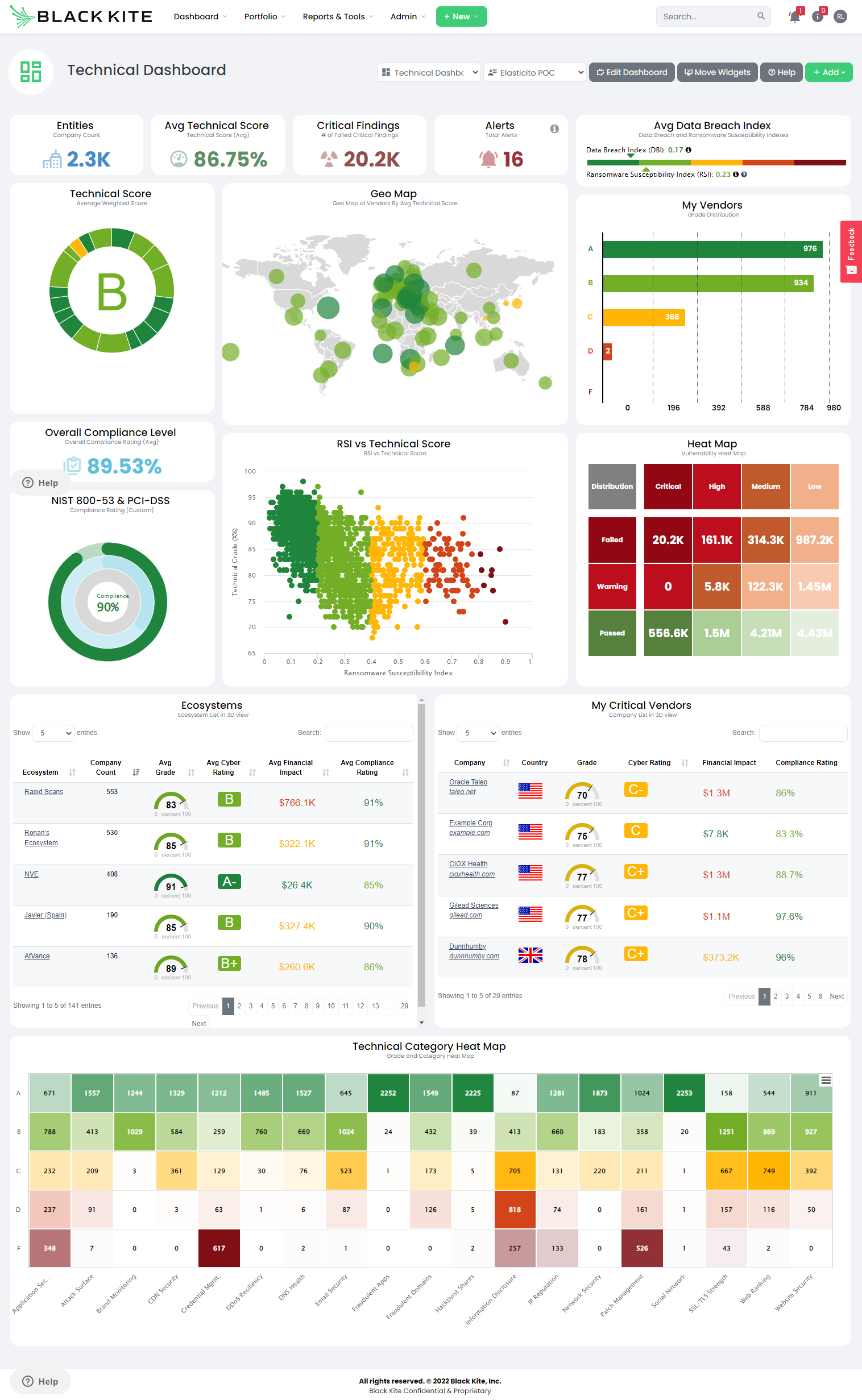
Combined with a cyber risk operating model (which Elasticito can help you to produce), where it is clearly understood what the level of acceptable risk should be for different types of vendors, it should be entirely possible to assess and monitor all vendor relationships for cyber risk without having to dedicate additional resources.
4. Reacting to industry and world events
The last 12 months have seen some tremulous events on a cyber risk and geo-political risk level that had the opportunity to significantly impact third party relationships. Starting off with the Log4J vulnerability at the end of 2021 and subsequent vulnerability disclosures with vendors like Cisco and Okta; and then the major geo-political risks associated with Ukraine and Russia, and in recent months, Taiwan.
Traditionally, reacting to these kind of industry and world events has involved having to survey all third parties to assess if they might be affected by the issue; and if they are, what their plans might be to address the issue. Like risk assessment questionnaires, these can take days or weeks when the business needs immediate answers to understand their risk exposure.
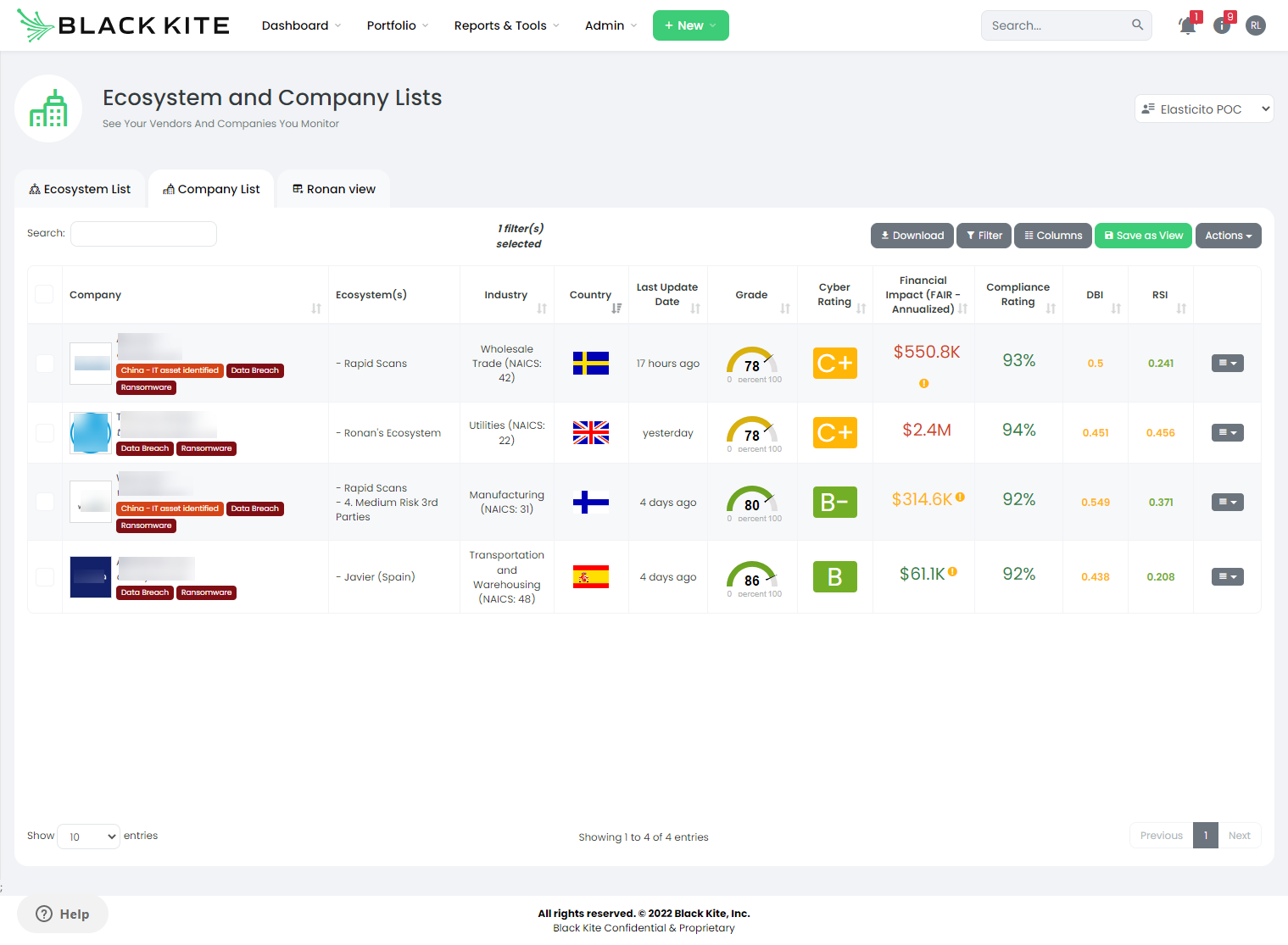
The Black Kite platform uses a neat feature called FocusTags that allow cyber risk professionals to search on key risk event tags. This immediately provides the risk team with a list of vendors who have publicly declared their exposure to the event; thus saving huge amounts of time and effort.
In the example below, we can see all companies that we are currently monitoring that have reported a ransomware incident within the last 90 days.
Conclusion
Third party cyber risk assessments can be time consuming, expensive and complex using traditional risk assessment methods, but they don’t have to be. With automation, using tools like Cyber Risk Rating platforms, an initial perception of cyber risk posture can be obtained within minutes and with evidence based data.
We are not saying that traditional risk assessment questionnaires should not be used. If they are well managed in a risk management platform, backed up with data and findings from a risk ratings platform, you will be best placed to be able to effectively assess and manage third party cyber risk.
If you have enjoyed this article and would like to understand more about how to use Security Ratings tools to automate third party cyber risk assessments and monitoring, you might be interested in this YouTube recording of one of our webinars on this topic, which you can access here.
