How to reduce your cyber risk with the FAIR cyber risk quantification model
Cyber risk is very real for organisations, who must constantly manage the risks and threats of cyber related attacks. According to the World Economic Forum’s “The Global Risks Report 2021,” cyber security failure ranks high among the top ten risks for business in terms of likelihood, outranked only by extreme weather events, livelihood crises and infectious diseases. But if cyber risk isn’t quantifiable, what’s the point? The key for any organisation is to understand exactly how much it’s exposed to cyber risk and how much it’s likely to lose. By quantifying that risk, you can set limits for your cyber security expenditures and calculate return on those investments. Read on to learn how you can make cyber risk more measurable for your organisation.

Cyber Risk Quantification: Understanding the FAIR methodology
A large concern in today’s boardroom is information and cyber security risk. This is because cyber risk is a complicated topic that has the potential to threaten the bottom line of any organisation. The FAIR (Factor Analysis of Information Risk) model breaks down this complex topic into easy-to-grasp pieces that board- and c-suite members will understand, enabling better decision making overall.
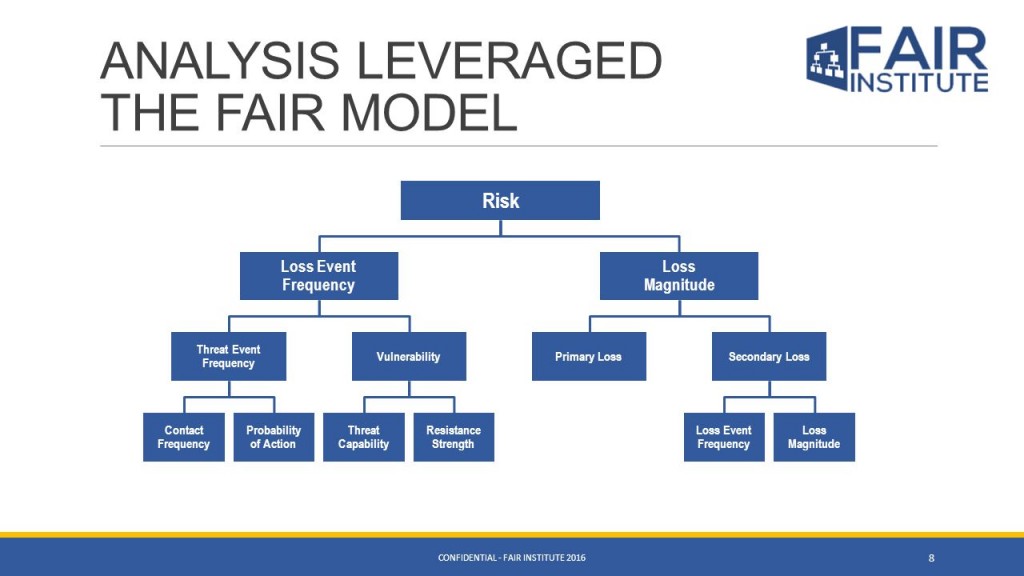
Figure 1: FAIR model (credit Fair Institute)
Essentially a model for quantifying cyber risk, FAIR codifies and monetises risk by mathematically measuring each element of an organisation’s risk posture. Each element is assigned a dollar value enabling the calculation of an organisation’s financial loss exposure. The FAIR model’s (Figure 1) components enable:
- A standard classification for information risk.
- A framework for establishing data collection criteria.
- Ranges of measurement for risk factors.
- A basis for analyzing complex risk scenarios.
- Integration into software such as Black Kite for calculating risk.
The FAIR model is peer reviewed and widely adopted across the globe. While there are many risk quantification models, the FAIR model has gained worldwide acceptance and has a growing reputation for providing the basis of sound risk quantification hypotheses.
With the continuing rise of digital transformation and the increasing reliance on using third party technology and service providers, external parties are increasingly handling personal or commercially sensitive data of your organisation. It is vitally important for all relevant stakeholders to understand the probable financial impact of a data breach occurring to your data. This is especially true when the data is being held and processed within a third party’s infrastructure: under GDPR and other data privacy regulations, both parties will be held liable and responsible if there is a data breach.
To understand the probable financial impact of a data breach with a third party, we must understand the cyber risk posture of that organisation – assuming your data is held digitally. Historically, this has involved largely inefficient security assessment questionnaires that can take weeks to complete and generally only give an indication of the internal policies and procedures of the company – not an external assessment of actual cyber risks. Managing cyber risk is as much about budgeting and prioritizing the various costs of security investments as it is about protecting against cyber risks: the process companies use to identify their greatest threats, calculate the impact of those threats, and make investments based on their likelihood of occurrence. While the FAIR methodology is not a substitute for risk analysis, it is a methodology for assessing the impacts and probabilities of a risk more reliably.
Immediate FAIR risk assessments for all third parties
Do you spend an inordinate amount of time checking off compliance requirements, guidelines, standards, best practices and control lists or questionnaires? While it is essential for a successful cyber security practice to conform to industry or government standards, there are many other important aspects to a comprehensive security program:
- In which areas of cyber risk management should we be investing?
- What are our top cyber risks?
- Is our organisation investing too much (or too little) in managing our cyber risk posture?
- What is the potential monetary impact of a data breach on my organisation?
Cyber security threats frequently materialize when company policies do not impose important software, or when non-IT executives ignore the advice of mid-level IT managers. Appearance of a cyber attack threat is often the result high-level executives who don’t understand the gravity of the cyber security threats on their doorstep in dollars-and-cents terms. Jack Jones from the FAIR Institute noted that the “two dimensions to maturity” within cyber security are:
- The ability to make well-informed decisions (executive level)
- The ability to execute reliably (engineer level)
In an age where digital technology is rapidly evolving, the FAIR model is enabling more organisations to achieve these two dimensions to maturity. In short, this means that an organisation’s cyber security department and the business units need to speak the same language.
Black Kite is the first cyber risk monitoring platform to adopt the FAIR model into all of its automated cyber risk assessments. Not only does this allow for a pre-emptive approach to information security, but for the first time also allows CISO’s, CRO’s and CFO’s access to a tool that quantifies the financial impact of cyber attacks in easy-to-understand business terms. Risk factors across the entirety of the organisation can be conveyed, as illustrated in Figure 2 below:
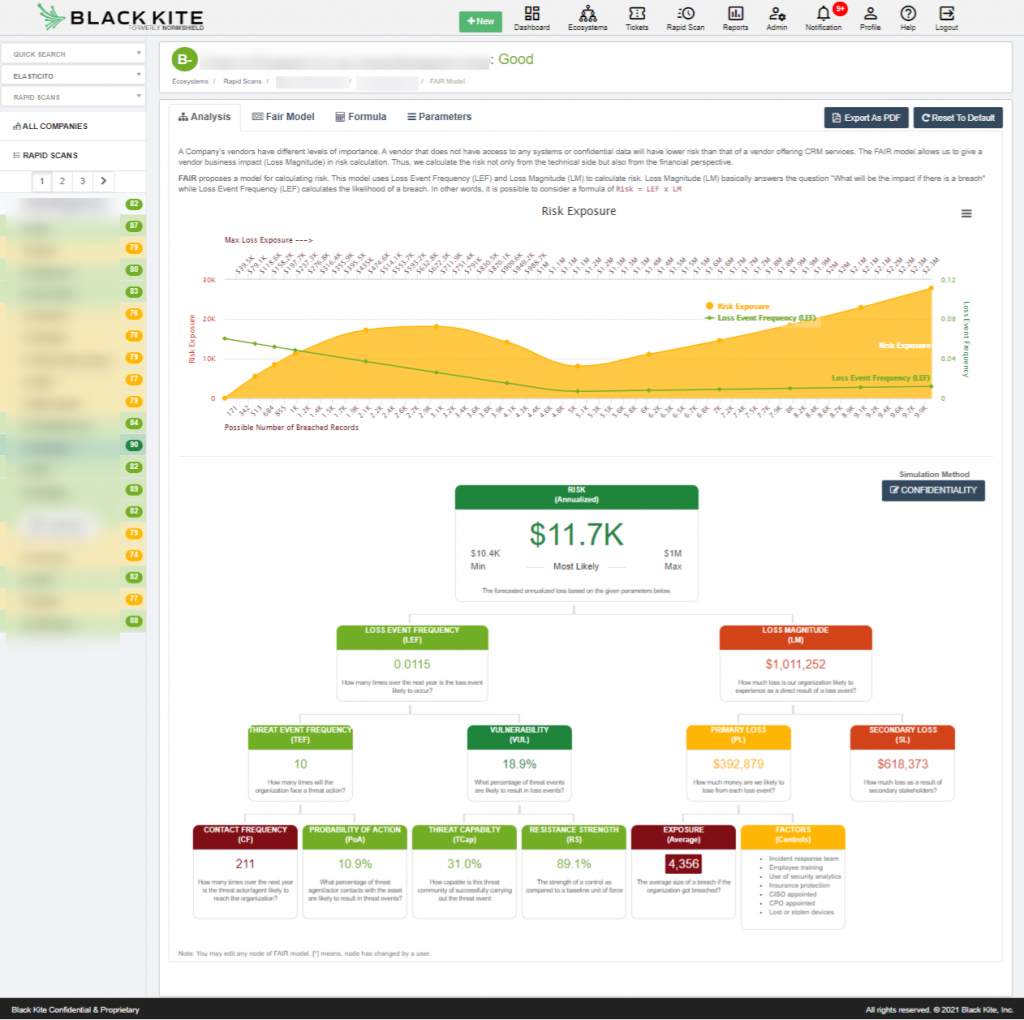
Figure 2: Black Kite’s FAIR model for quantifying an entity’s cyber risk
Using the FAIR model to aid vendor selection decisions
Third parties are essential to your organisational ecosystem. You need them in order to expand and grow. They can extend your reach, improve efficiency, and help you deliver the best possible products and services. However, they also carry a significant amount of risk. Organisations that involve cyber risk or information risk colleagues in the vendor risk due diligence process often do so as part of their compliance requirements. Unfortunately, cyber security risk assessments are often viewed as bureaucratic and disruptive to the commercial and procurement processes.
Using the FAIR model, it is now possible to communicate with colleagues in departments such as procurement, in a language that they understand. Meaningful and defendable financial risk data can be provided, enabling these departments to effectively calculate the financial risk that a vendor poses which can be compared with the commercial proposition being offered.
To illustrate, in Figure 3 below we can see how using the Financial Impact values in addition to the cyber risk rating of a range of short-listed vendors, we can now make more informed recommendations back to our colleagues in the business unit about the most optimal vendor choice from a cyber risk perspective:

Figure 3: comparing vendors with the FAIR cyber risk quantification model
Today, cyber security is a critical issue for any organisation. There is no telling which threats could arise or how they could affect your organisation’s infrastructure and information assets. IT professionals, you are on the front lines of protecting your organisation from those threats, and future-proofing your information assets. By investing in effective cybersecurity software, thorough audits and vendor selections can be conducted utilising the FAIR model. By doing so you will ensure your entire organisation speaks one language, more effectively addressing potential and probable threats, along with understanding the immense financial impacts these risks carry. Contact the Elasticito team to find out more.
