Simplifying Third-Party Vendor Risk Management
For many organisations, setting up, managing and maintaining a third-party vendor risk management programme using questionnaires can be a complex, costly and time-consuming exercise. Vendors are often required to respond to similar questionnaires from multiple organisations. For vendors, this can be a tedious and complex process that takes time and, ultimately, money to answer. In this article we will look at some of the security questionnaire basics and explain how to avoid sending burdensome questionnaires, making your vendor management system more efficient and your questionnaire evaluation process more accurate and far less time consuming.

Why is there a security questionnaire in my inbox?
According to the Ponemon Institute, the average cost of a data breach in 2020 was $3.86 million. Third-party vendors are now, more than ever, a vital component of an organisation’s supply chain. In fact, research conducted by Gartner shows that third parties have greater access to organizational data assets and are working with an increasing number of third parties. It is therefor not surprising that vendors represent an ever-increasing cyber security threat to an organisation, which is more often than not overlooked and, or inadequately risk-assessed.
In today’s interconnected world of supply chain collaboration, your organisation is at risk from data loss, system breach and infiltration, including ransomware from third party vendors. Because organisations must evaluate and manage these risks, many more organisations are sending these security questionnaires, placing an ever increasing burden on the vendors due to lack of standardisation.
With costly data breaches frequently occurring, organisations are thoroughly evaluating their vendors in an attempt to reduce and manage the cyber risk. A vendor can be thoroughly assessed verified, but could still be compromised vis. Solar Winds. The limitations of third-party risk evaluations need to be considered as “point-in-time” assessments, as penetration tests and questionnaires can never tell the complete story. Continuous assessment of critical vendors is one example of how the process could be improved rather than annual re-assessment only.
Third-party vendor risk assessment is a regulatory requirement mandated by various governments and industries, for example the EU and GDPR. Security questionnaires form part of the procurement process of most organisations and occur at least once a year. In essence, the security questionnaire evaluates if the vendor meets or exceeds an organisation’s risk appetite and complies with an internationally recognised set of cyber security standards and best practices.
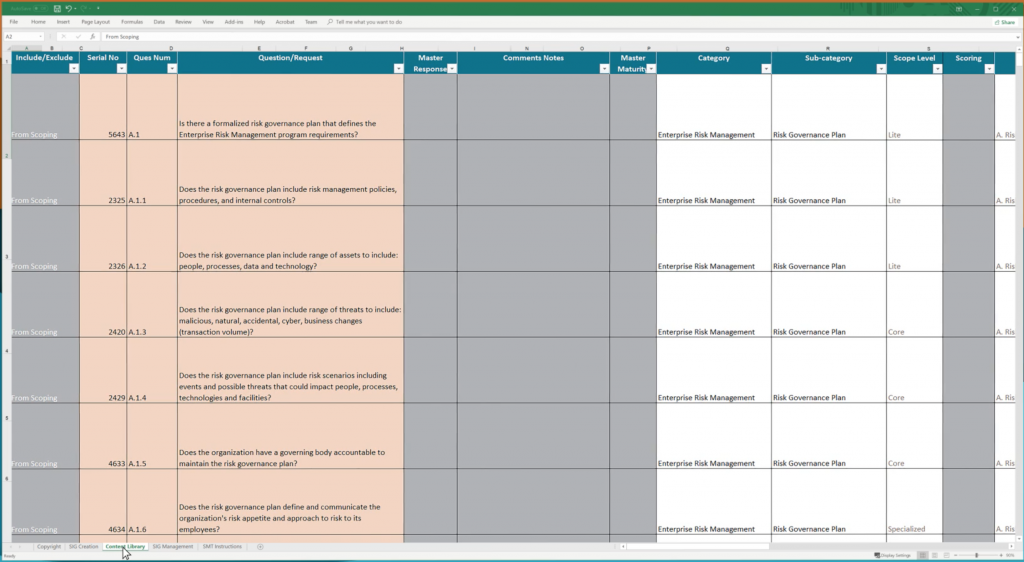
Responding to security questionnaires
The experience of completing a security questionnaire can be exasperating. As you might imagine, these questionnaires vary from company to company. However, all security questionnaires seek a clear answer to one question — do you meet or exceed the organisation’s risk appetite?
With the purpose of security questionnaires established, you must be wondering: “why is it so complicated to answer them?” Because your clients demand accuracy. Imagine trying to correctly answer the following password policy question: “Your password must contain a minimum of 8 characters with one capital and one special character. However, the vendor’s password policy contains 8 characters with one special character and one numeric character.” How should the vendor respond to this question when his policy could be considered just as secure as the requirements of the organisation? If the answer is binary, “yes” could be considered an answer if the vendor is answering optimistically. Objectively, the answer is “no” and if we were to apply a percentage to this equation, anywhere between 75% – 100% could be considered acceptable. This example clearly illustrates one of the challenges faced by both organisations and vendors.
Questionnaires can slow down the procurement process for organisations and communicating the results in a common language that is understood by both technical and non-technical individuals is one of the many challenges that presents itself. Vendors may gain a competitive advantage by maintaining a good cyber risk posture. While answering and evaluating questionnaires can be a lengthy, complicated and subjective process, does it actually have to be?
A new way to approach security questionnaires
Implementing a continuous vendor monitoring process can be an efficient and cost-effective way to both accurately assess your vendors if the correct use is made of automation tools. Reputational damage and regulatory fines can be an expensive and unnecessary experience. Investing even a small amount of revenue and resource evaluating third-party vendors can provide a huge saving on regulatory fines and other associated breach costs.
It’s possible to implement an ongoing monitoring strategy that can identify potential problems in real time, and also keep up with tracking risks organically through proactive recommendations or alerts. Starting with a simple and inexpensive solution, requiring little capital investment from your business, which provides you with insights into cyber risk posture using a common language understood by all parties, is a good route to follow.
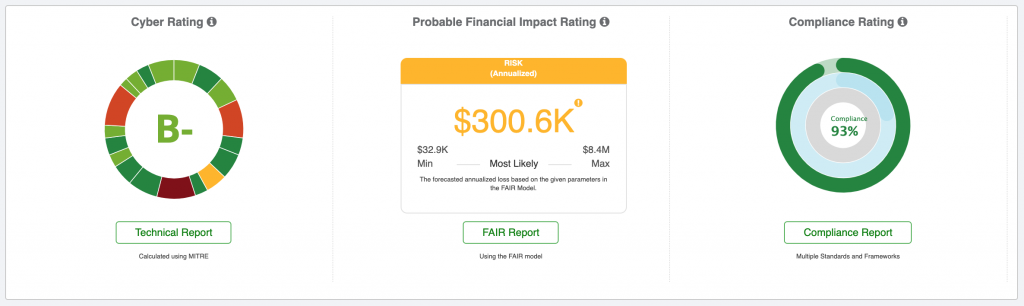
With the Black Kite Risk Management platform, organisations can gain a 3D view of their vendors’ cyber risk posture and enable continuous compliance monitoring. For more information about making your security questionnaire process more efficient using Black Kite, contact Elasticito.
